Please take advantage of the clickable Table of Content below for specific topics. Go to their respective sections under Counterseal Applications for concrete operational steps. Due to the novel nature of the Counterseal technology, please read through at least once the Background section to learn about the architectural framework, trustless or provider-less technology, various types of crypto wallets and the foundational supports. The OPSEC section may be helpful in formulating your security posture during the deployment of your Counterseal framework.
BackgroundThe InversionPhishing Bait & HookCounterseal Plexi-TechnologyThe Discipline of PrivacyThe PerimeterTOFU (Trust on First Use)PII and the RegistrySecure Link/BindIdentity WalletAi-Fi SubstratesFoundational SupportsPayment and FeesCounterseal ApplicationsIntroductionPlexiMailBindingGmail/Outlook/Hotmail/MSNYahoo!/AOLOthersTracking thru EmailsEMail a Non-PlexiMail AccountSessions and Decrypted ContentCryptoVaultPlexiWalletCryptoSignCryptoSign SubstratePreambleAnonymization and Authentication Contract ThreadsStarting and Ending a ThreadQuickSignCryptonBackup and RestoreSnapshotsShared Workspace of CountersealCounterseal DesktopDesktop PCSecurityTails Live USBPlatform FortificationHardware Redundancyai-fi.ccPlexiMail Web3 EditionSupported PlatformsConfiguration SetupPerformanceCrypto WalletCompatibilityWeb3 StorageMultiple IdentitiesTOFU (Trust On First Use)Trust EstablishmentOne-way ConfirmationPlexiMail++ ArchitectureStandalone Application Option Configuration Backup and RecoveryMobil USB for Tor"Paying" for PlexiMail++ and AnonymityRelease NotesOPSECBlogsSoftware downloadsEmail bindingFunding the Identity WalletProtecting Your Secrets
Background

The Inversion
In theory, exchanging personal data for frictionless commercial convenience is not always a bad bargain, provided we know how to consciously price our online privacy, gauge the amount we are voluntarily sharing, read the Privacy Policies conscientiously and hope the GDPR will deter all violators. In reality, unfortunately, it is impossible to go through the day without having our personal data unknowingly harvested by governments, companies and inevitably criminals with the promise of a free service. The exploitation of our privacy is so pervasive and systemic that we need a new vision for self-preservation. Our Counterseal framework prescribes how this vision can be realized by architecturally "inverting the Internet" and turning the surveillance capitalism upside down in order to rebuild it. We start out by offering an end-to-end-secured communication channel to our trusted peers that requires no mediating services and leaves no metadata on any radar screens.
The Counterseal framework offers a dApp suite to help us balance between privacy and community building while connected online. It adopts Signal's end-to-end encryption, implements a privacy-centric trustless blockchain with Stellar Smart Contracts and provides privacy self-auditability based on our open-sourced Counterseal Wallet Transparency standard, modeled after the RFC 6962 (Certificate Transparency) for detecting mis-issuance of SSL certificates. It will fundamentally change our security posture in fighting against phishing attacks, the weakest link in our defense against cyberthreats.
There will be no privacy without the ability to securely tuck away our secrets, especially those of high values like master passwords and crypto secret keys. The Counterseal suite contains a variety of tools to anonymously share and store our private data, with the portability afforded by the Counterseal Incognito Cloud and multi-factor protection through hardware redundancy.
Phishing Bait & Hook
Privacy is no longer simply about keeping our personal matters out of sight and relationships hidden. It has become the preferred entryway to numerous cyber attacks. Technologies are radically advancing unparalleled invasions of our privacy, the loss of which almost immediately attracts barbarians to the gate attempting a variety of attacks from any conceivable corner around the globe. Phishing is one of the most sinister attacks usually launched after breaching the victims' privacy. It is the oldest trick in the book, the effectiveness of which is significantly amplified by sharing the same information intelligence woven into the fabric of Surveillance Capitalism, the prevalent business model of the web. The phishing emails look and smell exactly like any ordinary soliciting commercials constantly being delivered to unsuspecting individuals. They share the same surveillance technologies. Some will try to push its target into action by creating a sense of urgency threatening account expiration and placing the recipient on a timer, which causes the victim to be less diligent and more prone to error. We let our guard down heedlessly when contacted by someone who appears to possess certain knowledge about us. The more detailed and intimate the perpetrators learn about us, the more effective the attacks become.
The Internet is practically a fowler's snare. It is clearly unrealistic for us to live off-grid nowadays in order to avoid the risk. However, to protect ourselves from the relentless onslaught, we must extricate our private data from public services, commercial or otherwise. The top 10 data breaches of all time included Yahoo, Adult FriendFinder Networks, Facebook, Myspace, LinkedIn, Adobe, etc., the usual suspects. The number of compromised accounts are in the order of billions. In addition to spying on us, to all intents and purposes, all those popular service providers are not far from "sharing" their collected private data on us with cyber criminals by being the easy targets of cyber attacks. GDPR and similar measures only lock the barn after the horse is stolen. We need to rebuild the barn and re-architect the Internet afresh.
This Counterseal app is a suite of mobile apps highlighting the privacy aspect of our end-to-end-encrypted personal network infrastructure assisted by Ai-Fi.net. It takes advantage of the latest advances of technologies that have reached a sufficient level of maturity such that no longer is it absolutely required to involve any service providers in mediating our social interactions. The smartphone in our pocket has over 100,000 times the processing power of the very computer that landed man on the moon. To take advantage of this moon-landing-capable technology in our pocket, a newly-architected, peer-to-peer, distributed architecture can certainly release our blind reliance on free services, the root of Surveillance Capitalism, and stop most phishing assaults in their tracks. We recognize that the loss of privacy due to phishing not only compromises our dignity, safety and self-determination but more importantly also sets us up for additional targeted hackings and identity theft. This Counterseal mobile app is a proven example of how this next-generation privacy-centric approach can be implemented, beginning first at protecting our privacy, the weakest link in the cyber security chain.
Counterseal Plexi-Technology
In addition to the tremendous advances in processing power, the cost of hardware has also dropped to a new low level that ushers in the IoT revolution. However, by and large, we have not taken full advantage of this low cost structure to answer some of the toughest security challenges. Architecturally, hardware/software sharing is still the dominating architecture. It is very convenient to lump all the useful applications into a single mobile platform like iPhone or Android, backed by an infinite supply of third-party applications from the "app stores". Unfortunately this concentration of functions onto a single dedicated device creates a huge "attack surface" due to its generic complexity. Any compromises of critical hardware/software components would affect all other applications residing on the same device. The well-known Pegasus spyware was originally an attack on a single app, the WhatsApp, which managed to "root" the device in the process and took over the whole hardware as a consequence. The battle is over when the underlying OS is compromised, collaterally damaging all other applications in the combo.
Many security attacks can be effectively averted by taking advantage of multiple pieces of hardware or functional redundancy. The success of dual-factor authentication, universally adopted by banks in making use of multiple and redundant proofs of identity, is largely attributable to this doctrine of redundancy.
Since our initial aim is to demonstrate how effectively a brand new privacy-centric and provider-less infrastructure can be implemented, taking advantage of component redundancy as the go-to weapon, we take pains in creating a new vocabulary to explain the unconventional approach we've adopted. We describe our "provider-less" approach as "inverted" to underline our bottom-up peer-to-peer bent. We apply our Counterseal framework as a prism for looking into the complexity of our cyber environment and the rich connectivity of the Internet, which offers a myriad of powerful solutions for eliminating the service providers from the equation. Note that Counterseal is not devoid of cloud-based services. It is just a different architectural choice such that the system-wide Counterseal services don't involve themselves in application layer operations, especially those that directly lead to surveillance and tracking possibilities such as account database, man-in-the-middle components or mediated data cache. We describe those system-wide, privacy-centric, lower-layer services as "Foundation Services". Outwardly, the Counterseal architecture exhibits a set of very light-weight foundational services supporting various "fat clients" exclusively controlled by the users.
Affixing "Plexi" to our tools intends to give an overtone to our technology indicating the substantial reduction of the attack surface through judicious use of device redundancy and extra layers of end-to-end encryption. In the context of Counterseal architecture, anything "Plexi" involves multiple interworking components and many layers of fortification.
Specifically, we call our brand of secure email as "PlexiMail" to hint our success in preserving the "federation" property of the email services, which is lacking in most other so-called secure emails and social media in general. We coined the name of our crypto wallet as "PlexiWallet" to point out its superior security protection based on component redundancy and elimination of single points of failure. Taking advantage of our PlexiMail as a secure and private network transport, we offer the CryptoSign eContract package for application scenarios when the negotiation process must "absolutely, positively be private".
The Discipline of Privacy
The Perimeter
Keep in mind that the Counterseal architecture only addresses a limited aspect of the privacy requirement on the part of the individuals. Privacy protection is a fight against illicit social engineering. Intrinsically it must be a group effort involving all parties and participants sharing the same interest where the group is founded on. This is especially the case when we want to retain the convenience of certain publicly accepted practices, such as the all-important federation property of email protocol that supports interoperability across independent servers, each of which is under an independent jurisdiction. The Counterseal technology is designed to operate under specific "Relationship Maps" created and maintained by you the users for purposely defined situations. The "federation" support allows the Relationship Maps to cross a diversity of email communities cutting through a variety of email services.
TOFU (Trust on First Use)
We assume different roles under different social situations. The identity to be protected must be qualified by its intended group of groups of which it is a part. The more fortified the firewall isolating the group from others is, the more secure the protection becomes. How insulated a group is from others and how overlapped various groups are allowed ought to be the outcome of a careful risk assessment.
Different identities a private individual assumes may be inadvertently linked. Multi-factor authentication is one such scheme many service providers employ to cross-reference you with your other identities. Criminals naturally have a much bigger wiggle room in triangulating their prey with little repercussion. Cross-reference is the prerequisite of cyber targeting. Prepare to present many different avatars for your participation in various groups that demand a higher level of privacy if you don't want to be targeted. Obviously, there are no hard and fast rules about how many identities for you to adopt or how many tools to utilize. It is to be balanced between convenience and security, the latter of which is usually measured in monetary or reputational terms. The Counterseal framework is not yet capable enough to cover all the community aspects of our Relationship Maps. Hopefully it makes your self-defense easier.
The TOFU protocol is the formal procedure for an individual to carry out before starting interacting with a partner. It is meant to be conducted "out of band" without relying on the application context at hand. In other words, without relying on any service providers, TOFU requires you to confirm or accept the identity of the party attempting to establish contact completely on your own through other channels outside the context of Counterseal. To establish trust, TOFU suggests the use of non-Counterseal telephones, Signal, non-Counterseal social media, whatsapp, Twitter, dead drops, spycraft or any method that is believed to be sufficiently reliable as the basis for transferring the trust to the new Counterseal sessions.
Counterseal is designed for protecting your high-value assets or rights and may cause some inconvenience under certain circumstances. Self-defense does carry a certain amount of cost.
PII and the Registry
To conduct social interactions, we represent ourselves through names, avatars or descriptors that identify us as an individual, a member of a community, a party to a contract negotiation, a holder of a service account, the owner of a property, etc. The term PII (Personally Identifiable Information), such as the Phone#, SS#, driver license number, email addresses, residence, Twitter hashtag, Instagram ID, etc., is inherently "public" and easily leads back to the person in question. In the case of encrypted communications, the PII about the parties involved reveals a large amount of metadata even while the content being exchanged is impenetrable.
Any information used to distinguish us from others outside its intended context may potentially be an infringement of your privacy. The Counterseal framework requires individuals to publicly announce and tightly control the exposure of their PII through the Counterseal Registry. For instance, to authenticate your end-to-end encryption sessions, you may securely link/bind an email address to your public keys (your Counterseal identity) through the Ai-Fi/Counterseal Registry for ease of resource discovery, access, and self-auditing. Striving to be a trustless dApp, the Counterseal Registry is offered through a smart contract, which is currently hosted on Stellar Open Network, which the 11th largest cryptocurrency in terms of market cap. It may migrate to the Ethereum for more operational flexibility and easy access to off-chain storage.
Due to the necessity of maintaining off-chain data and external interfaces to traditional Internet services (oracles), it is not currently feasible for Counterseal to be implemented completely as a smart contract. Instead, Counterseal adopts an alternative approach, taking its cues from CT (Google's Certificate Transparency), by allowing the participation of any qualified parties to jointly create an eco system for the maintenance of PII registration. It allows multiple blockchain-based public registries, independently constructed but publicly auditable, to jointly protect and offer public access of registration data.
Secure Link/Bind
There are two hosting options:
- Real-net: This is to employ Stellar blockchain in safeguarding your digital assets. It incurs a small amount of crypto coins in XLM.2.
- Test-net: This is for trying out Counterseal without paying any real crypto coins.
Note that the Real-net and Test-net do not interoperate. Please bind this app to one of your email addresses. It will only be tied to a key pair in your Ai-Fi wallet and nothing else. This is to ease your private interaction with other Ai-Fi users and afford you a customized protective shield. Behind the scene it is managed as a Digital Asset on Ai-Fi Blockchain so that your ownership of it may be publicly established and verified. Your email identity under Ai-Fi is rigorously protected through Ai-Fi Blockchain.
Identity Wallet
Counterseal takes a different approach in protecting your PII by allowing you to create many pseudonymous identities (public/private key pairs, or your Counterseal Identities) from a crypto wallet anchored on a public blockchain, currently based on the Stellar Network, which are devoid of any PII. The owner of a Counterseal Identity then explicitly defines and attaches extraneous PII to that unencumbered identity intended for an specific application context. For instance, one of your wallet identities may "bind" to an email address in order to work through it in the email context within our encrypted PlexiMail application. If it is bound to one of your "public" email addresses, your emails will only be end-to-end encrypted without extra protection of your metadata. If it is bound to a "stealth" address, or an email address acquired exclusively for a specific purpose not associated with any public PII of yours, your PlexiMail will be end-to-end encrypted without leaking any personally identifiable metadata. You will be required to explicitly request or accept any new bindings through the TOFU (Trust On First Use) protocol when first reaching out or being contacted by your partners.
The Counterseal Identity Wallet is accessible only through the Settings. It is not to be confused with the PlexiWallet, an alternative to hardware wallet designed to support public cryptocurrencies based on the Threshold Signature technologies. You will be prompted during the initial installation steps on where to store the recovery passphrase/seed of the Identity Wallet. After the successful installation of the Counterseal app you can still retrieve the passphrase through the creation of Cryptons as inputs by selecting "Attach Recovery Seed".
Ai-Fi Substrates
To provide provable privacy protection, the Counterseal framework is designed to avoid the meddling of any service providers. It is "provider-less" and therefore requires no sign-up or account registration. It accomplishes this design goal by adopting the following architecture:
- Any public information and their bindings to Counterseal identities are transparently published on the Ai-Fi Blockchain: This is currently implemented on the Stellar Network.
- Any shared infrastructures are structured as shared substrates built into lower enough layers that require no PII to operate or support.
- Any fees to be collected by Counterseal are levied on the "pay as you go" basis with cryptocurrencies which also flows through your Identity Wallet.
Foundational Supports
Generic supports through the Ai-Fi substrate include:
- Secret-keeping Crypton
- Storages in the Ai-Fi Incognito Cloud: Planned for the follow-on releases Ai-Fi will provide anonymous cloud storage with the protection mechanism similar to that of Crypton but with built-in redundancy and expendability.
- Tor Onion Routing: This is for hiding your sender IP addresses.
Additional foundational substrates are provided per individual application requirement. For instance, due to its complexity, many foundational services are offered to CryptoSign, as outlined here.
Payment and Fees
Obviously the cryptocurrency-based payment scheme shares similar thorny issues on interfaces with legacy systems, KYC (Know Your Customers) rules, external data sources, off-chain storages and decentralized oracles. Nevertheless, it is already a generation ahead of most other efforts in protecting our privacy.
The anonymization of individuals' cryptocurrency holdings is not part of the Counterseal service currently. Counterseal collects fees and payments from users' Identity Wallet, which is a full-function wallet for Stellar Network Lumens. It is users' responsibility to fill that payment wallet before paid Counterseal services can be requested, the amount of which is pre-calculated and clearly labeled before the service is rendered.
In the trial scenario based on the Stellar Test-net, the payment wallet is automatically funded for test purposes. The Test-net, as clearly labeled, is for test purposes only without the consensus guarantee. Its content also gets purged periodically. Since it is not permanent, the Counterseal Binding registry under Test-net may lose its content and behave strangely when that happens. Please keep that in mind during your tests.
Counterseal Applications
Introduction
The PlexiMail allows everyone to email securely and privately but maintains the most critical federation aspect of the emailing without forcing the requirement of a new secret email account . The CryptoSign utilizes the PlexiMail as a network transport for conducting contract negotiations through emails the old fashioned way but supporting strong digital signatures and multi-party multi-factor authentication. They are both self-managed, provider-less and account-less, a far cry from most other popular electronic signature applications (e.g. DocuSign).
The PlexiWallet, aka Counterseal Wallet, offers an alternative to hardware cryptocurrency wallets, fortified by the powerful Threshold Signature technology utilizing at least two air-gapped redundant devices to ward off cyber attacks or recover from loss of hardware. The CryptoVault is a simple password safe. All these mobile apps are collected in a single package due to their sharing of the foundational substrate implemented in the Crypton framework for provider-less and account-less self-managed cloud storage including the SSS (Shamir's Secret Sharing) scheme for more protection options.
There is another cryptocurrency wallet hidden under the "Settings", which is referred to as the Identity Wallet and provides the many PKC (Public Key Cryptography) identities behind the scene in protecting our users' identities and privacy. It is a real cryptocurrency wallet built on the Stellar Blockchain and not to be confused with the PlexiWallet intended for real cryptocurrency transactions. Making payment through the Identity Wallet, when fully implemented, will anonymize the payee and make "follow the money" considerably more difficult. After installing the Counterseal app, you need to bind one of your email accounts to the Ai-Fi Counterseal Blockchain Registry, which is built on the public Stellar Network.
If you know how to fill your Identity Wallet with real Stellar Lumen, you can start for real through the Stellar network. If you just want to test the waters before risking your real Lumens, try to bind to the test Registry and see what you can do with the pre-allocated 1000 test Lumens. Note that the Stellar Test-net gets reset/recycled about every 3 months. You must reset your test accounts and data every time that happens. There are no cross-Registry interfaces or migration allowed currently between the Test-net and the real Stellar Network. Find out more about the Registry and the binding process here.
(PlexiMail is aka Ai-Fi SecureEmail; CryptoVault aka DigiVault; PlexiWallet aka Counterseal Wallet; Crypton aka Krypton.)
PlexiMail
An extensive write-up of SecureEmail, the original package for PlexiMail, can be found in one of the blog entries under the heading "How Secure Is Your Secure Email" . A separate document details its implementation relative to the Ai-Fi framework as the foundational substrate and how it is architected as a digital asset rooted on a blockchain.
Both the PlexiMail and CryptoSign messages are encrypted emails passed around through your mailboxes bound to the Counterseal app. The raw encrypted entries for both the PlexiMail and CryptoSign messages are not viewable directly within your standard email client.
Your email server is only a transport in the Counterseal context. After a PlexiMail or CryptoSign email is opened and viewed, it is copied into a separate Counterseal database, which is insulated from other mundane email operations and can be independently backed up and restored (more on this later). This arrangement also lowers the chance of their accidental deletion while viewing unencrypted emails. Many users find it tidier to bind the PlexiMails to a separate anonymized email account created specifically for transporting encrypted emails.
All recovery operations and the reset of the PlexiMail binding require the proof of your possessing the Identity Wallet.
Binding
PlexiMail is an end-to-end email encryption application overlaid over an email account of your choice. This "overlay" architecture preserves the "federation" property of your chosen email service. PlexiMail works with any email services as long as the IMAP protocol is supported. To apply the PlexiMail protection, an email address must be set up and bound to the Identity Wallet built into the Counterseal app.
The PlexiMail protected email address is no longer a simplistic address. It is managed as a digital asset rooted on a blockchain and the associated email address protected like a digital asset. Unlike NFT, since the ownership of the email address involves a public email provider, PlexiMail and its inbuilt blockchain-based Root Registry serves as a monitoring apparatus to detect maliciously or mistakenly registered PlexiMail bindings. The PlexiMail binding system is more akin to the ecosystem of CT (Certificate Transparency) that makes the issuance of website certificates transparent and verifiable. In the case of the PlexiMail, there is no third-party issuer and the proof of identity and the circle of trust is self-initiated. Note that our open-sourced Counterseal Wallet Transparency standard emphasizes consistency over redundancy for privacy consideration. It also makes the follow-on TOFU verification a crucial link in establishing the trust chain.

If the goal is to simply encrypt the email and take advantage of the TOFU protocol for constructing a circle of trust, eliminating spams and phishing along the way, you may bind your PlexiMail to one of your email addresses already in place. To further your aim to protect the metadata, you may want to start out afresh from a new unencumbered email account and carve out a new relationship map based on PlexiMail.
Note that among the listed email providers, Outlook/Hotmail are the only ones that don't attempt to triangulate their users by requiring multi-factor "security protection". A simple account ID with password of acceptable strength is all there is for setting it up. In other words, a straightforward, no-frills email account such as Outlook is a good candidate as a "stealth" address. Obviously the standard location or other tracking avoidance schemes still must be judiciously applied. Counterseal offers only the limited defense through Tor anonymous routing.
You may avoid adopting a public email provider altogether to remove a natural attack point, in which case you need to set up a private, self-managed email server and define the necessary settings through "Others".
Gmail/Outlook/Hotmail/MSN
It is relatively straightforward to deal with these email providers. Enter your email account and follow the prompted instructions. Gmail appears to be the one with most approachable OAuth support.
Yahoo!/AOL
Legend has it that these two services of Verizon support OAuth. Unfortunately we have not been able to set it up for Counterseal. However, Yahoo!/AOL offer a sign-in path for "some older, third-party email apps (that do not use Yahoo branded sign-in page)". It basically requires an end user, you, to generate an "app password" from your Yahoo!/AOL account (in the Yahoo!/AOL Mail client) and enter it in the Counterseal binding screen in lieu of your "standard" Yahoo!/AOL password. This requires a bit more effort from you but works out nicely. Check out the details here.
Others
If your binding involves an email service not on the list, you need to select the "Others" and provide the detailed server parameters in their support for IMAP in terms of port assignment, access protocol and SMTP designation. Some email servers may not support IMAP.
Tracking thru Emails
There are many tricks in the arsenal of a hacker that can tempt you to click on phishing baits or track your whereabouts. An email of a questionable origin must not be trusted, especially those embedded content requiring a download from external sources that require a secondary web visit. In PlexiMail Settings, the option "Block all remote content" is ON by default to force you to think twice before retrieving any additional content not already part of the original email. With that default setting, any embedded remote content requires an explicitly issued permission to retrieve.
This blocking option may be separately applied to different categories of emails in future releases when multiple PlexiMail bindings are supported.
EMail a Non-PlexiMail Account
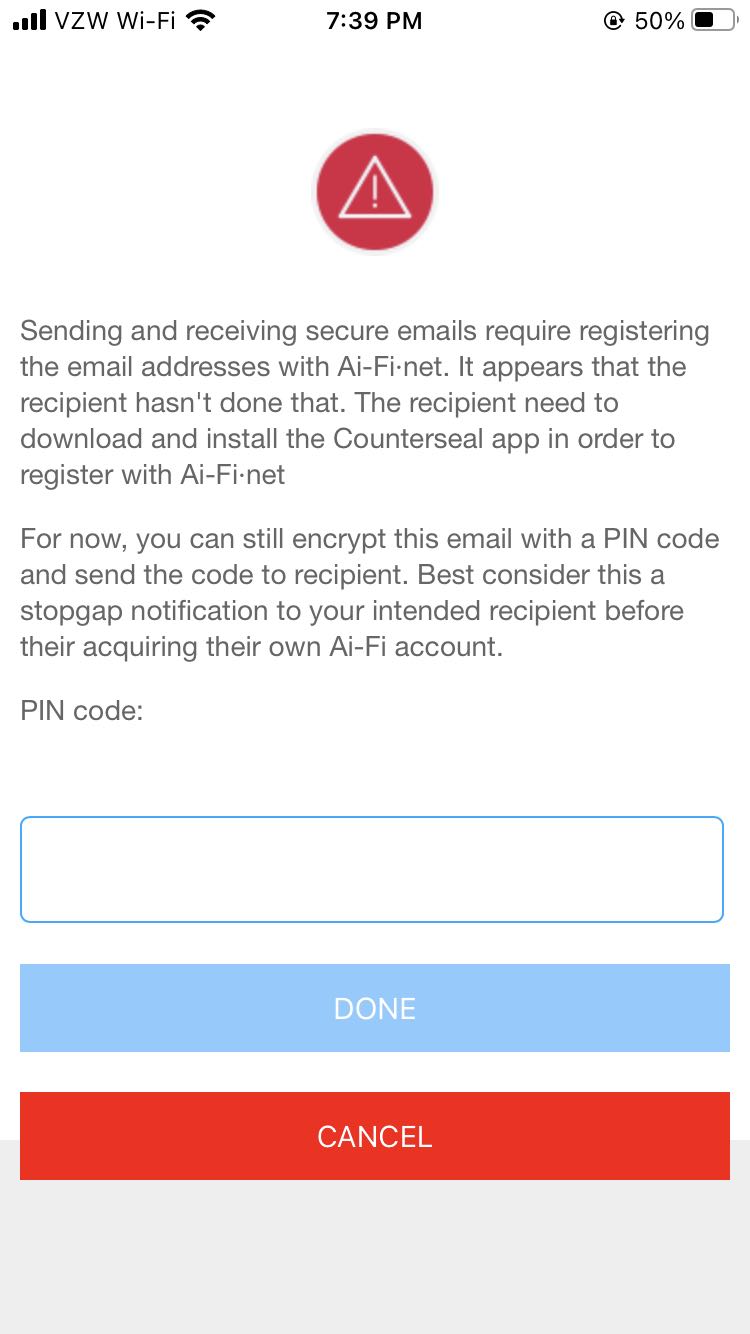
For the ease of contacting someone who is not currently registered to the PlexiMail blockchain, you will be given the option above to send your email encrypted to your contact, which may be retrieved with a PIN code you specify here. This mode of delivery of encrypted email is mediated through a PlexiMail service and no longer secured end-to-end. Make sure you understand the risk exposure in this mode and take appropriate precautions.
Sessions and Decrypted Content
The lifecycle of a Counterseal session starts with a TOFU (Trust On First Use), the successful completion of which establishes an encrypted channel for authenticated parties to engage in secure communication. Sessions are time dependent and easily interrupted by power failures, network outages, device malfunctions, loss of devices, suspicion of hackings, etc., that necessitate the termination and reset of sessions to enable renewed protection of the follow-on new channels. The asynchronous nature of the email as the underlying transport adds additional variables to the maintenance of sessions.
As a consequence, individual messages collected by a participating party may or may not be decryptable depending on their relative position on the time scale of the receiver bracketed by independent intervals of sessions, each of which is led by a new TOFU and invalidates all previous ones due to the loss of key generation or other security concerns. In other words, when viewing the historical records of messages, some entries may be deemed as "outdated" due to their positions on the session/time scales and their "trustability". Those "outdated" entities are frequently seen in the recovery process of a snapshot.
CryptoVault
CryptoVault is a simple password safe, internally structured as a Crypton token, with its encryption keys automatically generated and tied to an instantiation of the Counterseal app. Its content also enters into the snapshot when one is taken. It currently is not integrated with any cross-device cut/paste and therefore best used to safekeeping "master" keys or those long and difficult to memorize.
The edit session for a CryptoVault must complete before it gets stored. An expired foreground session may cause the loss of entered data.
PlexiWallet
The specifics for working with the PlexiWallet can be found here.
At our website there is a three-part blog titled "Breaking the Banks", which gives a historical perspective on the critical need of protecting our cryptocurrencies and offers a new paradigm for safeguarding this new class of personal asset. Most of us tend to describe where we keep our crypto assets as "crypto wallet", which simply does not connote the multifaceted security implication on how we choose to park our crypto assets. Before we re-establish the complete security infrastructure in the brave new world of "DApps" (decentralized applications), where the traditional safety net of heavily regulated financial institutions, commercial banks, safe deposit boxes, etc. can no longer be counted on, we need to take matters into our own hands. The Counterseal PlexiWallet offers one of those new mechanisms we hope you can confidently rely on.
CryptoSign
Traditional contract negotiation involves face-to-face meetings or direct communication between parties to the contract. Those meetings can be organized privately or even secretively in order to protect the sensitive nature of the negotiation under many circumstances. The figure below is the typical mental image of a contract/agreement negotiation in the traditional settings prior to the advent of electronic contract negotiation and e-signatures. The service providers as we know them now were conspicuously missing. They were not involved, required or even available at that time. The privacy of the contract negotiation is obtained by default.

Ever since the federal legislation of the Electronic Signature in Global and International Commerce Act was enacted in 2000, the e-signature regulation has made electronic contracts and signatures legally binding in the same way as paper contracts bearing wet ink signatures. The picture of an e-contract negotiation has all of a sudden fundamentally changed to the picture below:
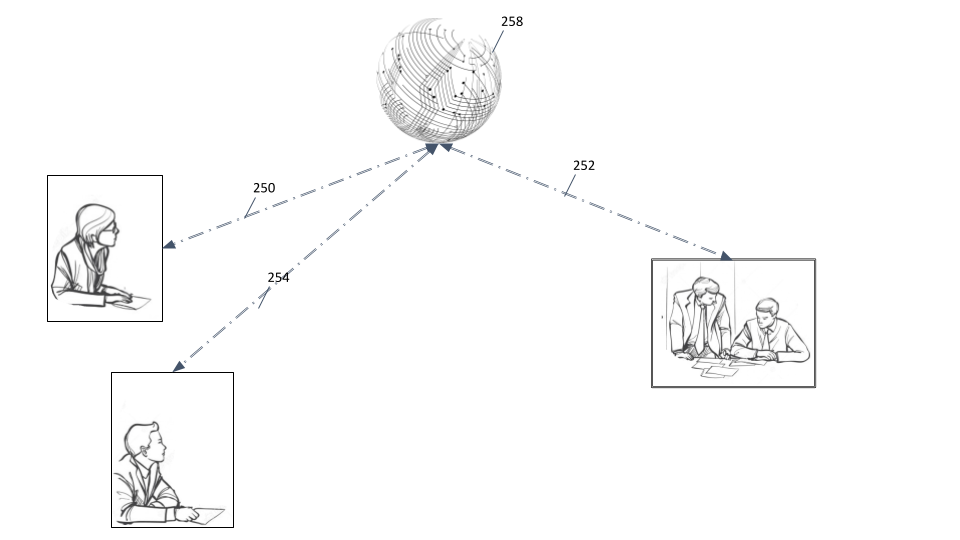
To take advantage of the convenience, cost-effectiveness, easy deployment, security, and single management facility across all communication devices, we are forced to accept the mediation of a "service provider" (258 in the picture), an e-signature provider like DocuSign. Unfortunately, the involvement of a service provider brings about many downsides as well when the bulk of the e-signing activities are outsourced. Among the many shortcomings of involving a service provider, the loss of privacy has the most severe impact, which can cause considerable challenges under scenarios such as the merger and acquisition negotiations, price biddings of goods and services, intellectual property transfer, technology outsourcing or many others where confidentiality is of critical concern. Not only the content of the contract, the identities of participants in those situations captured by the communication metadata are just as important to the negotiation that often entails severe financial implications, let alone the inevitable risk of the service provider being attacked, snooped or compromised by cybercriminals. Generally speaking, service providers are low hanging fruits for attempts of data breaches demonstrated by abundant hacking news from around the world.
In a nutshell, the Counterseal CryptoSign framework is part of an effort to bring the community back to its traditional private settings but still offer all the convenience of conducting contract negotiation electronically. This is made possible by adopting an asynchronous transport, namely the old fashioned and ordinary emails, and making all contract negotiations direct and private once again without needing any e-signature service providers.
CryptoSign Substrate
Like the picture below, all communications (240, 242, 244) are direct and protected by end-to-end encrypted channels. The CryptoSign framework still provides all the necessary support through "foundational substrate" (245 to 249) without requiring account sign-up, subscription based payment scheme or visibility into any aspects of contracting. A "fat client", namely your Counterseal app, absorbs all the contract-related functions or supports involving only those foundational substrate services that recognize no constructs outside of their narrowly defined APIs.
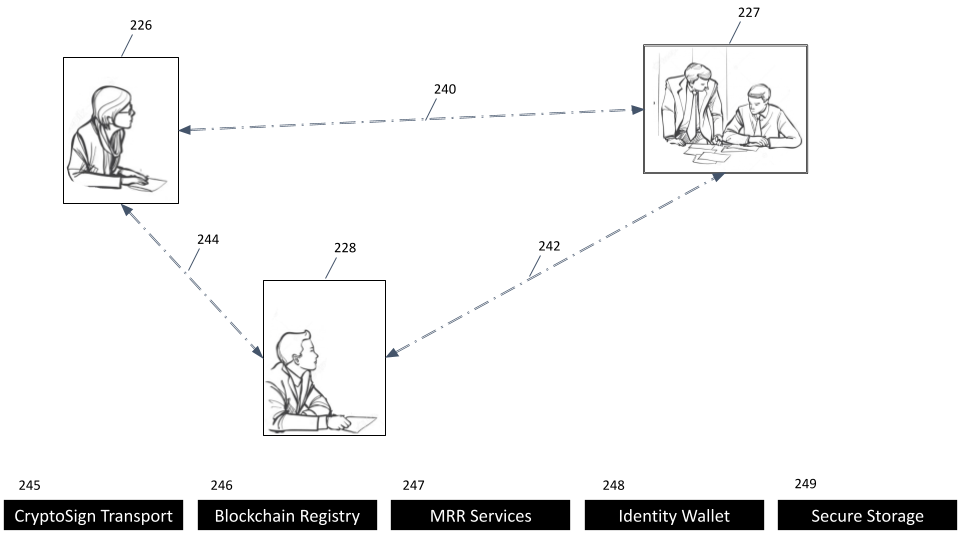
Note that 240, 242 and 244 use the PlexiMail as transports to pass encrypted messages around. In other words, both the CryptoSign and PlexiMail are applications built on top of our end-to-end private emails, but with a bit more processing for e-Signature applications.
Preamble
In keeping with its privacy-centric design, CryptoSign expects all parties to the contract prepare their own contract and only relies on the app to securely pass around the negotiation messages, to enforce the authentication policies so the identities of all parties are faithfully verified with evidentiary strength and to procure the e-signature based on the inbuilt strong PKC digital identities supported through the various crypto wallets.
The Preamble encapsulates and establishes the parameters of the parties' use of electronic records and signatures, security procedures and similar aspects of the transaction under the CryptoSign framework. It also identifies all the involved parties to the contract coupled with the authentication requirements to be satisfied before the finalization of the contract. CryptoSign focuses its work on the materials contained within the Preamble. The aim is to complete all the requirements laid out in the Preamble, combined with the actual contract details in the PlexiMail attachments, which are to be presented to all the parties to the contract in their totality in order to solicit the final agreement culminating in the collection of all e-signatures and requested biometric (video/audio) evidence. The final contract along with all the supporting evidentiary materials and e-signatures is packaged in an unalterable package, timestamped and optionally registered in the Ai-Fi Counterseal Registry for permanent record.
Anonymization and Authentication
Since CryptoSign framework is currently based on PlexiMail and works with any email service providers, it is quite easy to anonymize the parties in their message passing. The popular approach is to obtain a "stealth" email account (an email address without any tie-in to an individual's PII or Personally Identifiable Information) and pass around the contracts through that stealth email. However, the final contract must overcome this anonymization and attribute all parties to the contract to their PII. This challenge of "mistake as to identity" in contract negotiation is a highly vexed area of contract law, especially under the framework of CryptoSign where the privacy protection sometimes runs counter to the need of avoiding the mistake as to identity. CryptoSign offers a variety of authentication mechanisms, including the gathering of real time biometric data and multi-factor authentication so that the identities of individual participants are unassaillably-proven to parties involved but still remaining anonymous to anyone outside the purview of the contract negotiation. It also offers a foundational substrate service MRR (Message Registration Relay) supported by Counterseal or any disinterested third-party to formally attribute a participant to their published identity specified in the Counterseal Preamble. This MRR service can also offer the email registration service for PlexiMail.
Contract Threads
Starting and Ending a Thread
A contract thread is a time-based collection of PlexiMails relevant to a particular contract negotiation, subject to the protocol and convention of the CryptoSign. One of the contracting parties is delegated to administratively push forward the contract discussion. This Moderator starts a contract thread by creating and giving it a Contract Thread ID. A typical contract thread includes the start-up discussion, negotiation back and forth, finalization of the contract and the "Sign Invite" process initiated by the Moderator when he/she has come to the recognition that all involved parties have pretty much settled on the final terms and conditions of the contract.
The final "Sign Invite" is the most critical step, starting out with a Preamble as described previously. This final contract or the preamble combined with all its attachments must not be altered once the "Sign Invite" is initiated. If the need to modify arises, the current thread must be abandoned and a new one started from scratch. To assist the ensuing replacement negotiation, the previous Preamble and its attachments may be copied as the basis for the follow-up thread.
QuickSign
A typical contract negotiation involves many back-and-forths between contracting parties. However, some contracts are straightforward enough such that the signing is about the only transaction required as there isn't much to discuss beforehand. The contract itself is frequently just a standard form or some simple template already filled in, such as an apartment lease agreement or some sales receipt with quantity and payment terms specified. This is where the Counterseal QuickSign fits in, starting out at the "Signature Invite" session without any formal lead-in discussion. It involves only the last step of a full-blown CryptoSign contract thread.
Crypton
A Crypton is a nugget of data encrypted by a key pair of similar or higher entropy than popular cryptocurrencies. This is necessary since the Ai-Fi Incognito Cloud is provider-less and anonymous without the account-based indexes or multi-factor authentication that typically leaks PII, we are familiar with. More on this mechanism and its operations are presented here in an independent document. The recovery passphrase in the Identity Wallet and those for the Primary/Secondary of the PlexiWallet are typically stored in this Crypton format. The Counterseal Cryptons may reside in the Ai-Fi Incognito Cloud, your local disks, IPFS or any other storage arrangements anonymously with the same level of confidence as that for any public cryptocurrencies.
All recovery operations and the reset of the PlexiMail binding require the proof of your possessing the Identity Wallet.
Backup and Restore
This Counterseal app runs on your private mobile devices that safeguard your identities through the inbuilt Identity Wallet, based on which you can deliver private emails, stamp your digital signatures for any contracts and many other official functions where your identity is of critical importance. It also authenticates yourself in accessing your PlexiMail and corresponding with your contracting parties most confidentially end to end. The Counterseal app takes advantage of its inherent mobility and portability to accomplish those tasks that entail severe security consequences when "mistake as to identity" arises.
However, as with most mobile devices, your smartphone doesn't usually have sufficient storage resources to carry around with you all your confidential Counterseal data. It is not the greatest input device either for conducting lengthy or complicated document editing and is susceptible to loss, theft or damage. In consequence you should avoid relying on your mobile devices for archival functions. They are mobile access devices and portable identity seals or stamps but not suited as permanent data stores. Even with the PIN code and multi-factor authentication, it is advisable to only carry around sufficient amounts of data, periodically backup your Counterseal materials from your device, and conduct the restoral process when the need arises. In other words, do consider all your Counterseal data on your mobile devices as transient and take snapshots of them for backup at a frequency commensurate with the level and nature of all your involved risks.
All recovery operations and the reset of the PlexiMail binding require the proof of your possessing the Identity Wallet.
Snapshots
In the context of Counterseal Backup/Restore functions, the "snapshot" is the operative word. Since your mobile phone is only a snapshot (cache) device and not an archival one, the backup process only collects those data that have already been accessed by you and puts them away in a format suitable for long-term storage. Your backup collection is not a succession of profiles reflecting incrementally ALL your data at some specific point in time. It is only a dynamic picture of those data you have accessed and learned of through the lens of your Counterseal app on your mobile devices. It is best to consider all snapshots independent of each other, each of which reflects the state of your email store when the snapshot was taken.
Ordinarily you go to your snapshots to read some of the email entries which may be no longer kept in the Counterseal app on your mobile devices, or readable due to difficulties in decrypting them due to changes in wallet identities or session renewals. Those snapshots may be used to re-establish your session contexts only in the following limited scenarios:
- Loss of phones: This is when you want to recover your app from a loss event, in which the previous wallet/identities may not be trusted and the last snapshot is not necessarily the latest. This is the case you may select one snapshot from your collection and recover from that, after which your whitelist will be cleansed and any new communication with your contracts require a fresh new TOFU (Trust On First Use) process.
- Change of phones: This is when you want to migrate to a new phone while the old one is operational, in which case you will be required to take a final snapshot from the old phone for recovery purposes.
- Recovery of phone: This is when the old phone is no longer working or accessible but still in your possession. There is no thread of theft or hacking except the inconvenience of recovery with the last snapshot not necessarily recent. In this case the last snapshot will be restored to establish the baseline and all new communication requires TOFU as well.
For those cases mentioned above, a new installation of the Counterseal app is required in order to launch the recovery process, which takes many steps. Select the "Recovery Wizard" and follow the many steps to be conducted in order to rebuild your Counterseal sessions. Note that immediately after a successful restore operation, your email servers will be accessed to collect those "new" Counterseal data created after the snapshot.

Another perspective of your mobile phone as a Counterseal device is that the emails are used only as a network transport and not as a storage medium. Although the data transported by PlexiMail may reside encrypted in the email server for an extended period of time, the retention policy and the length of time are strictly email service dependent and beyond the control of any of the Counterseal functions. Hence the Counterseal app, and you for that matter, must not rely on the email service for data storage. This is particularly critical as Counterseal uses the IMAP as the access protocol in interfacing with the email service. The emails on the original email servers may be accessed simultaneously by multiple applications or email clients through either IMAP or POP protocol, none of which may claim monopoly over those messages/data passing through the email transport. You, the owner of the email accounts bound to the Counterseal app, have the final say on how your PlexiMails will be stored or accessed through various email servers, where they will be situated on multiple of your devices and how they will be managed for the long run.
Note that there is a built-in auditing function within the PlexiMail app that detects the "hijack" event when the email binding recorded in the Ai-Fi Blockchain Registry has been changed without the knowledge of its original/rightful owner. PlexiMail would indicate this serious and hopefully infrequent event through a clear notification to the affected user, in which case it is strongly suggested that the owner should change its email account security and password settings by contacting the original email provider and re-establish the binding with the Ai-Fi Blockchain Registry. It is also wise to take another snapshot in order to salvage those emails already delivered. There may be PlexiMails no longer decodable due to registry binding changes. Contact those original contacts (both senders/receivers) to re-establish the TOFU (Trust On First Use), which is clearly in doubt and must be re-established.
Shared Workspace of Counterseal
The Counterseal mobile app works through its Counterseal Dataset. The ever progressing Counterseal Dataset is best considered as a cache or a workspace, which allows periodic snapshots for reconstructing its historical views of the data. The snapshots are copies of the selected content of the dataset. They are the units of Dataset which the Backup and Restore functions work with.
To ease the moving of data between the Counterseal mobile app and its companion desktop counterpart, Counterseal offers a Shared Workspace for transferring documents across multiple devices. Its master copy resides with the Counterseal app on your smart phones and is accessible through a web server running with the app.
Counterseal Desktop
Desktop PC
The Counterseal mobile app utilizes your smartphone primarily as an authentication/authorization device for procuring e-signatures and miscellaneous evidentiary materials. The actual contract comprises a variety of documents, which sometimes are best managed through your desktop devices. To interwork with your desktop devices a separate Counterseal Desktop software needs to be separately downloaded and installed.
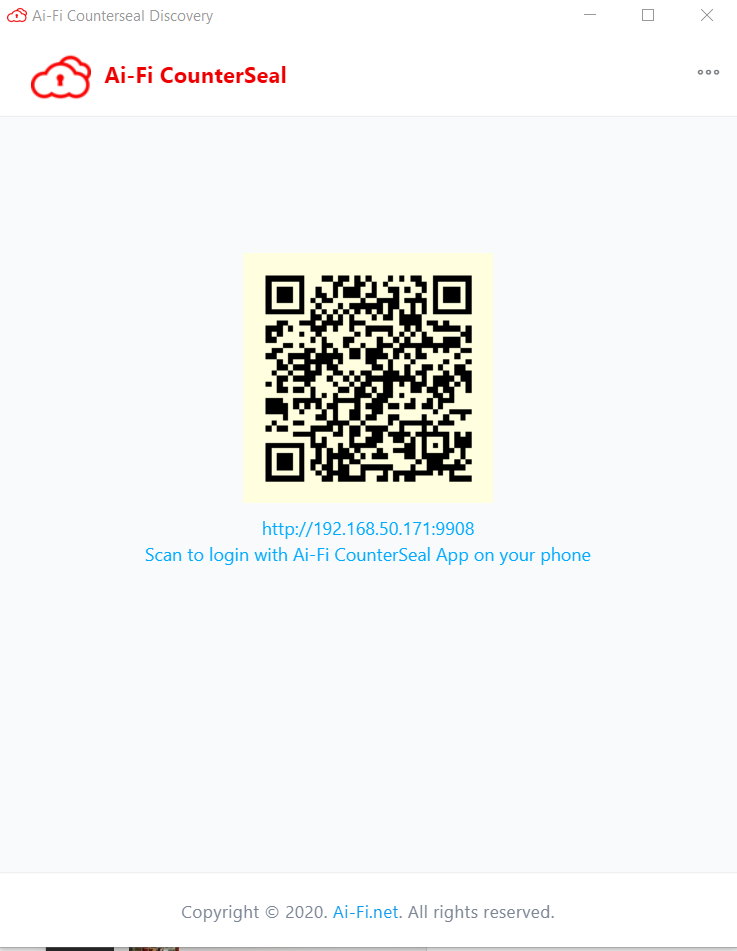
As of Counterseal 2.4.0 the primary backup store is your Desktop PC. Currently it is supported on Windows 10 /11 and on Tails Live, the most private, secure and physically insulated solution on a USB stick. Before activating the Backup/Restore functions, your Counterseal app on your smartphone must first "pair" with its desktop companion to authorize its operations. The upper left "QR Scan" icon on the main screen is designed for initiating the pairing process from its desktop counterpart, which requires a separate software application downloadable by following the "Get Started" button in our https://Counterseal.net web site. The desktop Counterseal companion application displays the below pairing QR code for your smartphone to scan when it is ready.
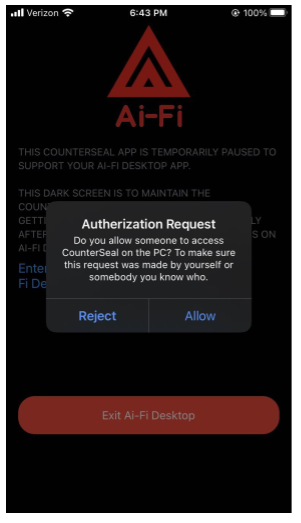
It is most straightforward to run both devices in the same LAN. If not, expect a bit more typing by following the instructions on your devices. The following is the screen displayed on your smart phone app after the phase I or the network connection of the pairing has succeeded and the app waits for your authorization. Once the "Allow" button is pressed, the app stays in this "dark" screen to indicate that the Counterseal app is taking over your mobile device and stays in the foreground until the interactions with its desktop companion completes. There is an option in the Settings to turn this lock mode off under the heading of "Authorizing Desktop Access". The default setting is "Lock to Dark Screen", which makes the interface with the Counterseal Desktop more predictable at the cost of consuming a bit more battery power.
Security
Currently the Counterseal Desktop is only protected through physical security, namely, through the simple physical possession of your desktop PC. You can augment it yourself, for instance, by password-protecting the Counterseal running folder, which can be found or relocated in the Settings, or moving all Counterseal files to designated locations which you can trust and copying them back before applying Counterseal Desktop operations on them.
We plan to extend the Crypton function to cover those files so they can be backed up into the Ai-Fi Incognito Cloud.
For enhanced security and privacy, adopt the Tails Live USB as described below.
Tails Live USB

Platform Fortification
The Counterseal cannot always protect you if you install a version of Counterseal from a computer with viruses or if you use it on a computer with malicious hardware, like keyloggers.
Tails is the state-of-the-art privacy-centric Linux distribution. The Counterseal framework provides a "Desktop" distribution based on the Tails Live System to supplement our primary Counterseal mobile app that runs on your mobile phone. It includes all the Counterseal Desktop functions bundled into a USB stick, which can boot from any 64-bit x86-64, IBM PC compatible computers (but not ARM or PowerPC currently) to be a fully insulated device. The idea is to keep all the secondary Counterseal logic outside the mobile app encapsulated in a portable hardware device. When needed, locate a compatible PC and boot Tails into the Counterseal environment with data either coming from the Counterseal Cryptons or the encrypted persistent data storage on the same USB stick. In addition to the Counterseal Desktop, the same USB stick also hosts the Secondary PlexiWallet as well for your cryptocurrencies. The PlexiWallet has stronger protection for your cryptocurrencies than most hardware wallets. Note that even after the integration of the PlexiWallet into the USB stick, the wallet itself is still maintained as a stateless and standalone software-only bundle, which will not function unless it is first activated by retrieving its "state data" from the Crypton in the Ai-Fi Incognito cloud. Losing your USB stick is inconsequential under this architecture.
To run from a Tails Live USB, you must go through the following steps, depending on your security requirement:
Go to the Tails website to first select a PC hardware and produce a Tails Live USB stick which boots Tails into your chosen hardware. This is probably the most involved step since not all desktop PCs or laptops are set up for booting from a USB stick.
Go to the Counterseal website, to download a version of Counterseal Live package and produce a bootable USB stick including the Counterseal Desktop app and the Secondary PlexiWallet.
- Make sure the code checksum matches the official one published at the website.
- The Secondary PlexiWallet runs automatically after booting the USB.
- The Counterseal Desktop is listed in "Applications"==>"Internet"==>"Counterseal" from the main Tails screen after booting up.
For those owning substantial cryptocurrency holdings or in need of heightened security protection, they may want to "manufacture" their own Secondary PlexiWallet to avert the Supply Chain Attacks, as the security procedure of hardware wallet delivery process is grossly inadequate in many cases. The Counterseal Secondary PlexiWallet is open-sourced and built on top of the Tails distribution. Our users can build their own Secondary PlexiWallet from sources provided by Counterseal. Please visit our Counterseal website for details.
Hardware Redundancy
Note that running from a bootable USB stick still does not rule out all the risks inherent in any hardware platform. The attack on BIOS, and the recently discovered Meltdown and Spectre vulnerability are not isolated cases. They are symptoms of the popular design principle for just about all computing devices that share hardware components. The well-known Pegasus spyware was a similar exploit on this share-everything architecture. It is originally an attack on a single app, the WhatsApp, which managed to "root" the device in the process and took over the whole hardware as a consequence. The battle is over when the underlying OS is compromised. This class of vulnerabilities will continue to plague us as long as we carry on piling additional functions onto a single hardware platform.
Although acquiring a separate hardware platform to run your critical app, such as the Bitcoin wallet, would disengage your app from a cluttered shared platform and reduces the risk of being collaterally damaged, it still faces the inevitable weakness of SPOF (Single Point of Failure). For instance, a hardware crypto-wallet running on a dedicated hardware is still vulnerable to dedicated attacks, an example of which is captured on this YouTube video to "recover" $2 million. This same hacker has just released another video of success of "recovering" $6 million of Bitcoin (??).
A more elegant solution is to distribute the same function over multiple devices, such as the Counterseal PlexiWallet with functions distributed to its two separate components, the "Primary Signer" and the "Secondary Signer", both of which have to be compromised before the attack may succeed. Its distributed architecture also affords the deployment to components with less protection, such as running the Primary on a shared mobile phone. PlexiWallet replaces the dependency on hardware by a redundant pair of "soft" Cryptons.
ai-fi.cc
PlexiMail Web3 Edition
This is to document a Counterseal Web3 dApp, a web application accessible by visiting https://ai-fi.cc. Here we'll go through the background concept minimally required before your engaging with this PlexiMail Web3 framework, the understanding of which would help you set up the configuration for its operations. The preparation steps outlined below is used to create a configuration context for our dApp when you are accessing our website the first time.
We sometimes refer to this embodiment of dApp PlexiMail as PlexiMail++ to distinguish it from its original version that was layered over traditional email services in a federated environment, considering its advanced Web3 architecture afforded to us by the recent availability of vast amount of cloud storage space, an offering spearheaded by Filecoin, touted as "a decentralized storage network for humanity's most important information". Practically overnight, we are liberated from the chokehold of service providers by owning our own almost infinite amount of network storage, to all practical purposes, for corresponding with out social contacts. Coupled with the ample bandwidth we, as individuals, have already paid for in connecting to the Internet, we can now reclaim our email communication and thwart any unwanted surveillance on both our data and metadata. In the following when there is no confusion within the context of the PlexiMail++, we may simply reference this Web3 Edition straight as PlexiMail without the "++" suffix.
Before we smooth out all the rough edges of our latest release, our users need to carry out a few more steps in setting this package up than what they are accustomed to, as the handholding of traditional email service provider is no longer there to assist you for obvious reasons. Current release assumes that our early adopters care greatly about their privacy and are willing to go the extra mile to protect it. Needless to say, there is an extra step for acquiring web3 storage from Filecoin (currently) so that E2EE (End2End Encryption) can be conducted without leaking metadata. (Traditional service-provider-based email architecture is actually an e-postcard, with both the content, sender and all recipients in the clear.) Although the risk of phishing attacks is low, we take advantage of the Ethereum Smart Contract to effectively block both the phishing attacks and DDOS (Distributed Denial of Service) in one fell swoop. Another immediate win is that there is no longer a limit on how large the data we ship around (practically), including all the attachments.
In future releases, we plan to create many application profiles so our users can quickly select a suitable one to fit their application scenarios with the level of protection they desire personally for themselves. For now, they are expected to follow the below steps to set up the PlexiMail++, necessitated by not having any mediating service providers (considered as MITM or Man In the Middle).
Supported Platforms
Currently PlexiMail++ Web3 Edition is web based and runs on any platforms where the Chrome browser, Edge, Firefox and a few Chrome based custom browsers are supported. Some users install the Brave browser and specifically dedicate it to PlexiMail++ in order to take advantage of its built-in Tor.
Configuration Setup
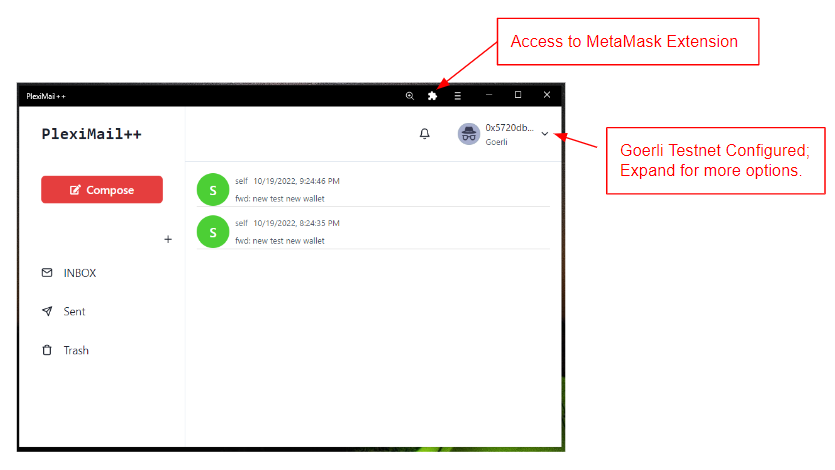
The above main PlexiMail++ operational screen is self-explanatory. However, before arriving at this PlexiMail main screen, you need to complete the configuration in preparation for the following parameters:
PlexiMail Address: Your PlexiMail++ addresses are created from your Ethereum accounts, jointly managed with an external crypto wallet, currently standardized to the MetaMask wallet. In all supported browsers, it is available as an (Chrome) extension. Follow the initial PlexiMail++ steps for installing and enabling the MetaMask wallet. After its installation, you need to fund the wallet with some cryptocurrencies for reasons explained here, depending on the Ethereum network you select. You and your partners may select one of the test networks to practice, for that we recommend the use of Goerli testnet. Try https://goerlifaucet.com/ to get some test coins. You will find it substantially easier if you first sign up for an Alchemy account (prompted on the faucet request page). Note that a testnet does not guarantee the permanency of you data established through the Smart Contract running on it and you can only communicate with those other accounts running off the same Ethereum network.
If you install MetaMask Wallet as a browser extension, PlexiMail++ would link to it automatically. Your Address is also "published and registered" with the PlexiMail++ infrastructure by executing a smart contract built into the Ethereum blockchain.
Private Web3 Storage: To get the free Web3 cloud storage, go to https://web3.storage. It relies on your email service to authenticate you. The granted free Web3 storage is identified by its "API Token". Locate it on the Web3Storage dashboard under "Account".
The above steps involve two external applications we choose to work with. Both are incorporated into the setup of PlexiMail++ by visiting https://ai-fi.cc and answering the in-program questions regarding those external applications. Note that the Web3Storage offers a variety of pricings for different storage capacity. Your email plus all its attachments can be successfully sent without size limit as long as it fits in your subscribed Web3Storage.
There are two more steps remaining within the PlexiMail++:
Signal Runtime: This is the step for preparing the end-to-end encryption sessions based on the Signal Protocol. It uses the PlexiMail Address set up in Step1 as input to the PlexiMail++ smart contract for establishing the owner identity of the address. Accept the charges of some Ethereum "gas fees" for the processing cost by pressing the "Confirm" button under the MetaMask wallet app displayed on the upper right of the webpage.
PlexiMail Configuration: After the successful completion of all steps above, PlexiMail++ creates a Configuration file to record what have been entered. You will be asked to "Export" this file to a safe location, which would be required on a recovery run when needed. If you lose this Configuration file, all your accumulated PlexiMail++ mails or correspondence would be rendered unreadable when your local application cache is cleared.
Performance
Web3Storage grows out of the same tree as the NFT offline storage support. They are inherently "publications" of stored content meant for stable and long term references in IPFS format. For short-term transient data storage it is not a perfect fit. Currently the deletion of stored data is promised but not yet implemented by Web3Storage. This is promised to change in later releases.
Functionally your Web3 storage needs to be private but accessible to your friends and partners at the same time. To meet this requirement, PlexiMail++ chooses to work with the tokenized storage offered by https://web3.storage. Your emails are "published" in the Web3.Storage and encrypted with keys negotiated through the private sessions with your partners in IPFS format, which makes them accessible only to authorized people. These steps sometimes can take a while to complete, especially for large emails. As a general rule, please be patient with the PlexiMail processing. We will continue to improve its performance going forward.
Crypto Wallet
Under PlexiMail++, each user is represented by one or many Ethereum blockchain addresses. They are inherently "Burner Addresses" and may be discarded after specific use. They are not designed to be friendly or easy to use and are the opposites of those traditional PII-carrying (Personally Identifiable Information) account IDs. You can make them less cumbersome by collecting and naming individual entries in your Contacts List. The tie-in of those unwieldy PlexiMail++ addresses/identities to their corresponding PII in the Contacts is strictly "local" or "private" to the trusted social circle privy to the exchanged content. Our users' contact list is hence strictly local/private as well, created merely to ease the data entry for the communicating clients. To enter into a PlexiMail++ social circle, you need to be formally recognized and trusted/permitted through the manual and personal TOFU (Trust on First Use) process. Before we offer a more stringent mechanism for passing around those lengthy Ethereum addresses, make sure the exchange of TOFU messages is conducted out-of-band and confidentially, certainly not through the PlexiMail++ itself.
Note that the PlexiMail++ address format takes after the traditional email and is presented as:
This is only displayed under the Settings-->Profile button in the upper right control panel of the ai-fi.cc webpages after the setup is successfully completed.
With the Ethereum addresses as your email accounts/identities and the MetaMask the default wallet on your chosen platforms, your identities are automatically protected by 2 separate factors: your password and the private keys embedded in your platform where the MetaMask runs on. It will be further strengthened when we integrate PlexiMail++ with our own custom PlexiWallet in the follow-on releases.
Your PlexiMail++ addresses are maintained in their respective Ethereum crypto wallet. The current default is the MetaMask wallet, which has been around for a while and survived many trials and tribulations and is considered reliable for our application. We don't expect our users use their Ethereum addresses for making crypto transactions, which certainly leak PII.
MetaMask is supported in most of our supported browsers as "extension", which can be easily enabled or installed. If you are not familiar with the concept of Crypto Wallet, or Ethereum Smart Contract, or Blockchain in general, please try to install MetaMask carefully and follow their introduction of blockchain concept, which is very approachable. This is the minimum you have to pay for living off the grid of Surveillance Capitalism.
Immediately after the setup of the wallet, you need to fill the wallet with real Ethereum coins, depending on your choice of the network. Again, use MetaMask as a base to explore the funding possibilities, or explore various "faucet" options if you decide to try out the test network. Goerli is our recommended test Ethereum network. Note that, all the parties you communicate with through PlexiMail++ must be adopting the same Ethereum network. They are not inter-operable for obvious reasons (on where our Smart Contract resides).
Compatibility
Due to the drastically different architecture, PlexiMail++ is not interoperable with traditional email services. The requirement of utmost privacy is intrinsically incompatible with the federation architecture.
In other words, the traditional "federation" property is lost on PlexiMail++ and the crossing between PlexiMail++ and traditional email services requires a software "bridge", which will be provided when resources allow. However, the application of bridging must be disciplined and probably of limited utility, as the bridging of PlexiMail++ with a traditional email address immediately leaks metadata and exposes the PlexiMail++ to tracking and surveillance.
Web3 Storage
Currently Filecoin offers 5 GB of free cloud disk storage for each user interested in Web3 storage solutions on which PlexiMail++ is built. Before we make our UI more friendly, you need to go to https://web3.storage/account outside our website to apply for your private storage. Enter your personal email and follow the instruction (and ignore the Github option for now). Filecoin offers a well-designed frictionless onboarding process. Just need to locate where that "API Token", the identifier of your private storage, is and cut-and-paste it onto the PlexiMail++ configuration process according to our onscreen instructions.
All the PlexiMail++ content you send is stored in your own Web3 storage. The recipient will retrieve the content of received emails from sender's private storage. Although it is in plain sight, it is anonymous and fully encrypted by the dynamic keys negotiated through the secured sessions and managed through you wallets with strength equivalent to any public blockchain transaction keys. No one in the world, including Gmail, outlook, protonmail, and even us, to just name a few, knows anything about this correspondence between you and your intended recipients. This is how the PlexiMail++ metadata is protected. We certainly don't need to go to Switzerland for "Swiss Privacy". Although not originally intended, PlexiMail++ is provably warrant-proof, as there is simply nothing in the emailing process we involve ourselves in, unlike those traditional service providers.
As always, YouTube is your best friend in learning Blockchain, Cryptocurrencies, faucet, Ethereum, Goerli testnet, MetaMask wallet, Web3Storage, Filecoin, etc.
Multiple Identities
Depending on your intended PlexiMail++ applications, the upper limit of 5 GB of free storage may be an issue for you. You can always upgrade it to the next paid tier of 30 GB or even higher amount.
However, one of the recommended approaches to deal with the limit of storage space is to adopt multiple PlexiMail identities (addresses) and associate them with different repositories. It is always a good idea to compartmentalize the exposure of your identities per your application scenarios. It also has the added benefit of additional free Web3 storage allocation, as each of the first 5 GB of free storage is tied to your specific email account (hence restricted to a specific facet of your PII) when it is first applied for. If any of your application scenarios requires more than 5 GB of storage space, you probably need to evaluate your risk of putting all your eggs in one basket.
Within the various lineages of Chrome browsers, the best practice for managing your separate PlexiMail++ Identities is to maintain each identity as a Chrome Profile, each of which actually owns its private sandbox and hence its separate MetaMask wallet. It is suggested to maintain a single identity per profile, namely a single identity account per wallet. It gets complicated quickly if you maintain many Ethereum accounts within the same wallet in order to establish multiple PlexiMail++ personalities. If you insist on a single wallet, each time you switch between your various accounts within the same wallet you need to refresh your browser tab in order to bring in a new PlexiMail context within the same profile.
Each PlexiMail++ Identity establishes its end-to-end encryption sessions as a succession of epochs, necessitated by the changes in session contexts, data storages and key materials. The creation or, rather, transition into a new epoch, e.g. due to the re-allocation of data storages or loss of devices, requires a new registration process and incurs new charges by the Smart Contract, which only keeps track of the last active epoch. Each new epoch requires a new "Backup Configuration Data". Only the epoch created last is active in the sense that it allows sending/receiving new emails. All backup configuration data of previous outdated epochs are for recovery (of old emails) only.
TOFU (Trust On First Use)
Trust Establishment
This is the same mechanism as that under PlexiMail, previously documented here. Each time a PlexiMail++ party moves on to a new epoch, a new TOFU process must be conducted again.
One-way Confirmation
In scenarios that only one end of the communication is interested in their anonymity, the other end may publish its identity and PlexiMail++ addresses without treating their addresses as "burners" or private assets. The TOFU verification/confirmation on the public site simply involves a SSL access to its public site and retrieves their public PlexiMail++ addresses.
This is most common when a merchant wants to offer anonymity when dealing with their privacy-conscious customers. The motivation is similar to Facebook's supporting a Dark Web site.
PlexiMail++ Architecture
[TBD: Picture of PlexiMail++ architecture with web3.storeage, smart contract, configuration, push-server, etc.]
Standalone Application Option
At the end of the initial setup, users are given the choice of how the PlexiMail++ is to run: as a web app by visiting https://ai-fi.cc or alternatively as a "standalone" web application (PWA) with its own dedicated window like a native app, which has its own launchable taskbar entry with the ai-fi.cc logo  . When it is pressed to run, it just looks like an ordinary web browser screen with a single default web page presented but not associated with any other browser bookmarks or options.
. When it is pressed to run, it just looks like an ordinary web browser screen with a single default web page presented but not associated with any other browser bookmarks or options.
Configuration Backup and Recovery
PlexiMail++ implements its end-to-end encryption by adopting the well known and proven Signal open source. We carefully avoid any use of your PII (e.g. mobile#); the Web3.Storage also allows us not to be involved in the store-and-forward of any messages for absolute privacy without the presence of any service providers.
For E2EE (End2End Encryption) session setup, there are certain amount of session data required. To ease the management of sessions, each PlexiMail++ client maintains a minimal amount of configuration data to keep the session moving forward. Note that all your correspondence and individual encryption keys are maintained in the configuration, without which your historical PlexiMails may no longer be readable. So please be careful in backing up your configuration and reapplying it when needed. If it is to be backed up on the local PC, make sure to record the folder where it is stored. You are also given an option to back up onto your smart phone, in which case a dedicated mobile app must already be installed on your phone.
Mobil USB for Tor
In addition to PII, other possible metadata leakages, such as the IP addresses or the geographical location of the involved parties, must be individually defended. The most popular mechanism is the adoption of Tor, which is automatically built in and may be enabled straightforwardly in the Brave browser. Also, a version of PlexiMail++ will be made available to run on Tails, separately documented here, based on which the second protection factor becomes portable and stateless.
"Paying" for PlexiMail++ and Anonymity
PlexiMail++ is free in the sense that this PlexiMail Web3 Edition is freely offered, but the incurred consumables, like electricity, computing power, traditional disk storage, RAM, printer, ink, internet connectivity, etc., are not. This PlexiMail Web3 Edition is a Web3 dApp and consumes “Ethereum gas”, which is the charge by the Ethereum blockchain for your consumption of its computational resources. There are two Ethereum transactions that cost gas: Every time you re-register to a new Ethereum account, it requires the execution of PlexiMail++ smart contract on the Ethereum blockchain, the cost of which fluctuates and currently at around $1 dollar. Most users stick to one account and incur this cost only once at startup. Additionally, every time a PlexiMail++ is sent, we charge several gweis, which is the smallest denomination of ETH (1 ETH = 1,000,000,000 gwei) and is about a hundredth of a penny. This charge is to thwart DDOS (Denial of Service) and negligible to you.
PlexiMail++ is not 100% dApp, as certain amount of off-chain data must be maintained to carry out the E2EE (End-2-End Encryption) and other PII hiding schemes, like almost all useful blockchain-assisted applications. It is as close as any realistic "Trust-Minimized" distributed application can be.
Obviously if you run under the test Ethereum network like Goerli, the test ETH does not cost real money. However, the permanency of your email communication is undefined and the PlexiMail++ Smart Contract is not guaranteed to be attack-free or without malicious manipulation.
Note that, the acquiring of cryptocurrencies to fund you wallet may expose your identity if not done carefully. Any credit cards and bank accounts carries your PII. We offer a simple utility to ease your payment process during the onboarding process. Get more details here.
Release Notes
- Web3Storage is highly advanced and offering huge potentials for our reclaiming the Internet service infrastructure in terms of privacy and independency. However, utilizing of our own cloud storage space for storing our private messages without relying on mediating service providers has some teething problems, among which the occasional performance penalty is one. However, the upload/download speed is quite reliable, albeit with some unpredictable delays. Occasionally some patience is called for.
- Support for multiple PlexiMail++ accounts managed by a single wallet is of high priority to our future development plan. This implies extending our CryptoWallet for PlexiMail++, with the added Threshold Signature support.
OPSEC
Counterseal framework is designed to protect your right to privacy, the right to be left alone. It is not sufficient to cover all your tracks if you intend to participate in the Darknet commerce, conduct illicit cyber activities, or walk around with a target painted on your back like Edward Snowden. Regardless, certain amount of OPSEC consideration is recommended in order to define a risk exposure level acceptable to you. For circumstances not directly covered by the framework, you obviously need to devise additional strategies on your own for protections not concurrently offered by Counterseal. The topic of secure and private contract negotiation is critical enough such that we've specifically extended our PlexiMail to cover it in the CryptoSign package. Your continued support of the Counterseal platform will bring more tools and options in the future.
In the following we'd like to outline a minimal set of OPSEC procedures for deploying the Counterseal framework, some of which have already been noted before.
Blogs
There are a few blogs we've created that address mostly practical aspects of our product offerings. You will find them helpful in formulating your OPSEC posture.
Software downloads
Start out by downloading the Counterseal mobile app from the app store of your preferred mobile platform. Search for our app with the keyword "counterseal".
The Counterseal mobile app must work with a complementary secondary "Desktop" package:
- If end-to-end encryption (confidentiality) is all that you need, download the desktop package for your preferred desktop platform
- If metadata protection is desired, use Tor for all required Internet operations, including the software downloads and setup of your binding emails.
- If your familiar desktop platform is not completely trustworthy, which we all know is a very tall order, we'd suggest the installation of our Counterseal Desktop Live on a USB stick (Counterseal Live) based on Tails, or The Amnesic Incognito Live System. It has built-in Tor, anonymous browsing, persistent/portable storage on the same USB for safekeeping all your secrets and snapshots, etc. Build up all needed Counterseal components such as the binding email (with your Identity Wallet), software downloads, Identity Wallet funding, etc. through the Counterseal Live.
- If your OPSEC requirement exceeds the quality of our pre-built Counterseal Live, you can roll your own Live system by making it from ground up. Our Counterseal Live offers the buildable open sources. Please also understand the remaining risks even after you go to extra length to deploy the Counterseal Live USB stick.
Email binding
The pros and cons of adopting a stealth email addresses have been discussed previously. The binding emails are used as transports. Keeping received PlexiMails in your snapshots by taking them frequently so you don't have to rely on your email providers for storage.
Don't turn off the option to "Block all embedded external content" unless you know exactly what you are getting yourself into. You can be easily tracked without that option.
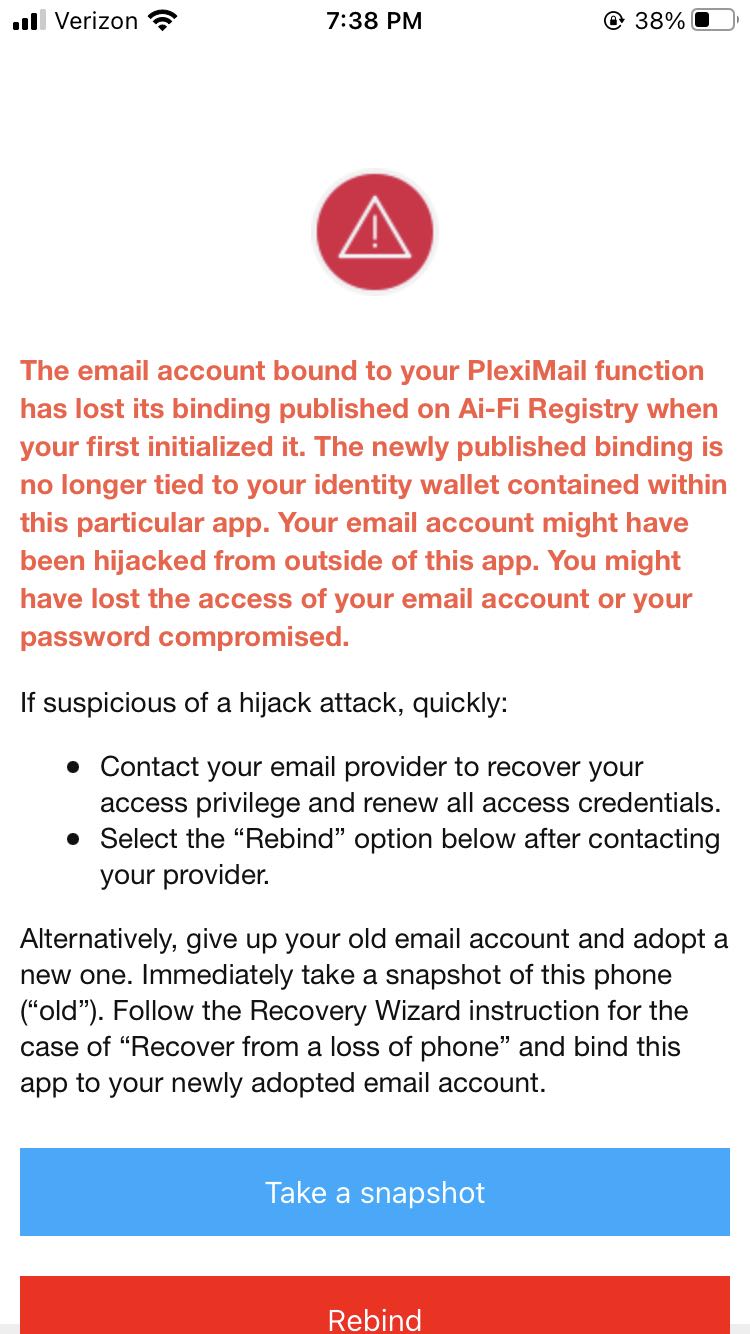
The email binding may be "hijacked" by some unsavory characters after losing your phone/Identity-Wallet (theft) or your email ownership (account hijack). After seeing this warning, you need to notify all your PlexiMail contacts and recover your email address by contacting the email provider if it is still critical to you. Hopefully your snapshots or backups have been taken frequently enough in the past so you don't lose much historical data assets. Calmly assess your loss, evaluate the impact and try to figure out why the breach has occurred.
Funding the Identity Wallet
In order to run on the Stellar Real-Net, you need to fund your Identity Wallet with real Stellar Lumens (Settings-->Wallet). The Identity Wallet built into Counterseal is a functional Stellar Wallet, to which you may send Lumens. To start out, at least 20 Lumens (less than $3 as of 7/1/2022) are required to register in order to satisfy Stellar's minimum balance. Most of the initial cost may be recovered if you decide to cancel your participation from the Counterseal framework. Unlike the initial registration cost, the cost of Stellar transactions is actually almost minuscule, typically calculated in Lumen Stroops (1/10,000,000 Lumens, or less than $0.00000002). This extreme low transaction cost has attracted a large number of central banks to adopt the Stellar Network as the basis for their digital currencies.
In principle, for personal and non-commercial use, Ai-Fi, Incorporated will not charge for Counterseal transactions beyond the first-time software purchase. Very infrequently, our users may be required to pay for a nominal fee as a means for us to counter DDOS (Dynamic Denial Of Service) when situation demands it.
Off and on, Ai-Fi may launch limited airdrop program to reduce the barrier for our users to adopt the Counterseal Framework.
To build up your trust network based on the Real Net, all your contacts and associates to be included need to be on the same Real Net in order to share the same Counterseal/Ai-Fi Identity Registry.
To bind with a "stealth" email address anonymously:
- Send the required number of Lumens to the Identity Wallet anonymously. There are numerous schemes to accomplish this through many different cryptocurrency exchanges. Since the required amount of Lumens is quite low, the KYC (Know Your Customer) is usually not a requirement.
- To ease your adoption of the Counterseal framework, we offer a payment service that accepts a credit card and converts your payment into Lumens to fund your registration. It promises not to track your payment history and destroys the link between your credit card and your Identity Wallet after use. You can always opt to pay through a non-reloadable prepaid cash card by making a trip to the supermarket.
- Select an email binding registry that you trust. The Counterseal Root Registry is based on an open standard that invites independent third-party registry implementation to participate as one of the Root Registries after passing a published certification process.
Protecting Your Secrets
The Counterseal app offers many critical tools to protect your secrets under the heading of "Crypton", which is considered the linchpin of the self-managed Counterseal privacy protection fortress. The importance of this protection mechanism can't be underestimated in the brand new world of cryptocurrencies where the governmental safety-net guarantees provided to depositors and all bank creditors are no longer available. The owners of cryptocurrencies are separated from their valuable assets typically by a PIN, a password, or a sheet of paper where the passphrases are written on with questionable cryptographic strength.
In the Crypton design, a secret passphrase is partitioned into two separate elements, each can be independently saved from the other and effectively create a 2-factor protection schemes through a simple mental maneuver. Like most valuable tools, it is based on a simple, sensible and often underestimated strategy. We have drafted a blog that recommends the best practices on how it could be deployed.

