Multi-Share Secret Distribution
Multi-Share Secret Distribution Protecting Our Crypto Wallet With Ai-Fi SuperLockThreshold Secret SharingDeployment ScenariosDigital Secrets and Periodic Rehearsal of Their RecoveryThe Shortcomings of Shamir's Secret Sharing?Ai-Fi Anonymous Cloud StorageUse Secure Ai-Fi Mail to Trade Your Cryptocurrency
Protecting Our Crypto Wallet With Ai-Fi SuperLock
When creating a crypto wallet, you are usually given a mnemonic passphrase of 12 to 24 words to store "safely" for emergency recovery purposes. Since it is in digital form, a loss event or a sneaky glimpse of it can have devastating consequences to your holdings in your wallet. Currently there is no simple and secure way of safekeeping it other than the standard advice of writing it down on a piece of acid-free paper and "storing" it somewhere, which is the crypto equivalent of putting all your eggs in one basket, or worse.
The Ai-Fi SuperLock is designed to protect any secrets of yours which are either not easy to memorize or perilous to write down. Keeping the recovery passphrases in Ai-Fi SuperLock is a popular Ai-Fi application for solving this difficulty.
Threshold Secret Sharing
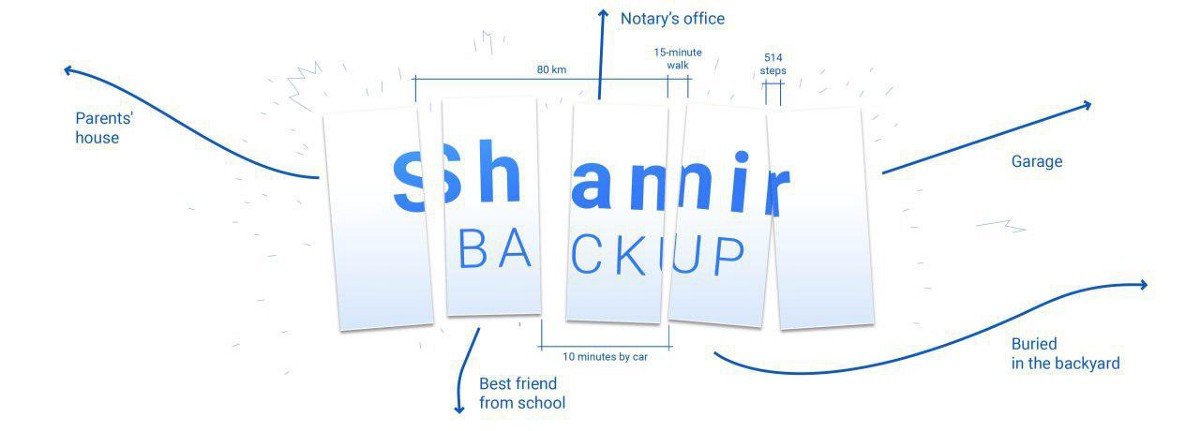
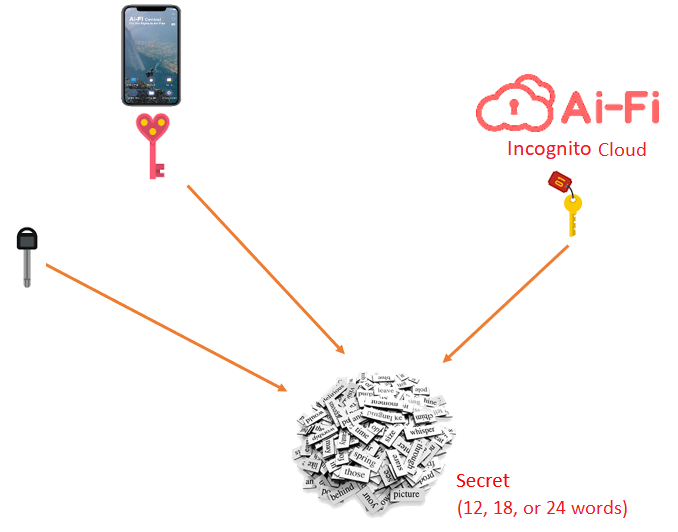
We are all concerned about losing our phone, or the loss of the recovery passphrase written down on a piece of paper. To make our wallet more secure, SuperLock adopts the technique of Threshold Secret Sharing or SSS (Shamir's Secret Sharing). We use a simplified version that first extends (encrypt/transform/obfuscate) the secret into 3 pieces of "shares". At least 2 of the 3 shares are required to recover the secret. Under this threshold scheme, any single mishap ("single-point failure") is not as catastrophic as before. Note that those shares are not generated literally by snipping the original key material into separate backup pieces (as in the diagram), rather by "transforming" it to multiple independent parts, each of which may be stored by itself.
Other than the first share that is to be kept on your phone, other shares may be maintained any way you desire. You may opt to store any number of shares in our Ai-Fi Anonymous Cloud Storage, which offers a very high degree of anonymity. Since the recovery process involves our mental faculty which is prone to errors, a periodic rehearsing of the recovery process based on this multi-share scheme is critical to ensure the recoverability of all the shares.
Deployment Scenarios
Deployment Example 1, against loss/theft event:
- Keep the first key share with your phone, protected by your phone's sandbox and hardware.
- Keep the second key share in Ai-Fi's Anonymous Cloud Storage. Ai-Fi is not able to decrypt its content and most importantly not its owner either. It is almost self-help, with the owner creating their own file name and password for protecting the second key share.
- Write down the third share on an acid-free paper in pencil and "securely store" it. The loss of this third share is recoverable by collecting 1 and 2 above.
Deployment Example 2 for protecting your digital assets:
- Keep the first key share with your phone, protected by your phone's protective hardware.
- Keep the second key share on your wife's phone.
- Keep the third share with your attorney, with whom you escrow your Will. al
Deployment Example 3:
- Keep the whole recovery key in the Ai-Fi Anonymous Cloud Storage, relying on your Ai-Fi cloud storage passphrase in the hopefully unlikely event that you lose access to your own wallet recovery key. The 100 bits of entropy of this Ai-Fi cloud storage passphrase is far superior to the traditional approach of writing down the wallet recovery phrase on a piece of paper. This is also without the concern of Ai-Fi.net as both a storage service provider and a "man in the middle".
Digital Secrets and Periodic Rehearsal of Their Recovery
Our SuperLock package is designed to protect any digital secret, not just our crypto wallet. It may be launched independently from the "DigiSafe" app and there is a shortcut from the Ai-Fi Wallet app leading to the generic application.
You can also set a schedule to rehearse the recovery process based on your selected deployment scheme. Ai-Fi will trigger the rehearsing based on the time schedule set.
The Shortcomings of Shamir's Secret Sharing?
There is no absolute security in the current state of crypto affairs. The many implementations of Shamir's Secret Sharing scheme are no exceptions. A few observations on comments made about Shamir's Secret Sharing shortcomings:
- Complexity in features is always the enemy number one in the realm of security applications. Our SuperLock function tries not to get fancy on features, just minimally required to avoid leaving the recovery seed by itself in an unattended "cold" storage. Our SuperLock defaults to the simplest construct of 3 shares, with the first one residing right on your mobile phone and the second in the ironclad Ai-Fi Anonymous Cloud Storage as an option.
- "Share Revocation" or "Social Key Sharing" is not an issue with Ai-Fi. When the need for recovery arises, the wallet will be restored and then recreated based on multiple key shares. A new set of key shares will be recreated in their entirety after the recovery. All previous key shares are retired without involving any revocation efforts. Furthermore, Ai-Fi's "Social Key Sharing" may be emulated by taking advantage of the fact that any one with a Home Server may host their own Anonymous Cloud Storage services that accept "social requests". A key share may be distributed to any Home Server that opts to support the Anonymous Cloud function with varying degrees of security and privacy constraints with specific or private ACL requirements. Note that offline and cold storage arrangement is always an option.
- Other troublesome issues discovered so far stem mostly from some poor implementations which lead to vulnerabilities and potential risks. Strangely enough the mistakes in creating or applying random number generators in cryptographic packages are committed at an extraordinarily alarming frequency. Our implementation has been paying careful attention in this department, which fortunately is not directly linked to Shamir's scheme. The secure recovery key sharing scheme is quite straightforward to implement if careful attention is paid to the important issues of random number generators.
- Side Channel Attacks are getting increasing attention. Software mitigation on that front can only alleviate a small part of the issue. Your concern about this particular attack surface is justified only if you lose your personal phone to an adversary equipped with an EE lab and able to disembowel your mobile phone without leaving traces. This particular risk is not specific to Shamir's Secret Sharing and is not what Ai-Fi's secret sharing is designed against.
Ai-Fi Anonymous Cloud Storage
Briefly mentioned above, an Anonymous Storage facility is offered by Ai-Fi to securely and anonymously keep your files of any content in Ai-Fi's cloud. It is based on modern cryptography, formally audited and peer-reviewed. The files submitted to Ai-Fi Anonymous Cloud for storage are completely anonymous and untrackable. Not even Ai-Fi.net has a clue where they are from or whom it is owned by, as long as the fees are kept up (with a very generous grace period). All users need to do is to specify the following:
- A strong enough passphrase (of minimally 100 bits of entropy)
- An email address (to work as a "salt" to prevent dictionary attacks and make your file unique but still retrievable, not needing confidentiality as long as it is unique per user)
- The content of the files to be stored
Based on this information a PKI key pair is generated with the hashed value of the public key as the file name and used to index the file in the Ai-Fi Anonymous Cloud. The files are encrypted based on an encryption key derived from the input parameters.
This storage facility has the following "warrant-proof" properties:
- Any file may be stored in Ai-Fi's Anonymous Cloud without needing a subscriber account, thanks to our crypto wallet.
- The owner defines their own passphrases, which are garbled before passing on to Ai-Fi. Ai-Fi has "zero knowledge" of the original file names and passphrases.
- The requesting party may further obfuscate their IP addresses through the built-in Tor anonymizing network before submitting the files for storage.
- The submitted files are stored safely indefinitely as long as the storage fees are kept up (with ample leeway for unpaid balances)
This secure and anonymous storage facility is most popular for our users to store one of their recovery passphrase key shares.
This is why Ai-Fi is entitled to claim "Not All Cloud Storages Are Created Equal".
Use Secure Ai-Fi Mail to Trade Your Cryptocurrency
While most crypto-currency traders use Google or Yahoo email accounts to trade cryptocurrency, it is definitely not the best way as it is not private and is clearly being tracked by those email service providers. Use Ai-Fi SecureEmail to keep your trade only between trusted peers.