Best Ai-Fi Security Practices
Best Ai-Fi Security PracticesAi-Fi SecuritiesPasscodes and Private KeysPassword ManagementSelf-reliancePasswords as Digital AssetsHierarchy of PasswordsOrganizing PasswordsComposition of PasswordsExampleA Password Strategy for PractitionersPassword Strength MeterPrinciple of Password Crackingzxcvbn and Password MetersThe Revised StrategyMiniLock Key StretchingSecuring the PassphrasesOur Raw Memory CapacityThe Memory Code of ImageryThe Memory Code of ContextThe Real Strength TestThe Fuzzy Search Utility
Ai-Fi Securities
Ai-Fi.net is designed to protect your cyber identity and digital assets. The tools and utilities under the Ai-Fi security architecture implements the following:
Various on-device "safes", including:
- The DigiVault within the app, with similar functions as those popular password managers.
- The synced data stores on the HomeServer, including your photos and videos uploaded to it
- All the data and devices to support the Ai-Fi Domain Security for safeguarding the domain perimeter and various IoT devices housed within it, including the ACLs (Access Control Lists) maintained on various devices.
Digital safes containing secrets protected by the SuperLocks, either through the Multi-Share Secret Distribution (Shamir's Secret Sharing) or the Cryptons in the Ai-Fi Incognito Cloud. They provide Ai-Fi Domain security taking advantage of your private devices and resources, and accessing the anonymous/pseudonymous storages in the Ai-Fi Incognito Cloud, which are popularly adopted to protect many different kinds of recovery seeds for a variety of cryptocurrencies.
The Ai-Fi Wallet in Ai-Fi Central, containing:
- All the DiD (Decentralized Identifiers) for pseudonymity guarantee in various use cases, protected by the proven Public Key Cryptography.
- All your Ai-Fi SecureEmails and their decryption keys, and importantly the ownership of your email addresses, a critical digital asset, through a blockchain based Ai-Fi Root Registry.
3 above is the foundational privacy and protection implements built into Ai-Fi, based on which those "safes" in 2 are constructed. The functions provided in 2, the SuperLocks, offer the linkage between the Ai-Fi Central and the Ai-Fi Incognito Cloud, which allows anonymous access to independent safes hosted in the cloud, accessible only through strong cryptographic keys.
The centerpiece of the Ai-Fi protection architecture is the mobile app Ai-Fi Central that provides the interface to the Ai-Fi security infrastructure. Its safety is guarded by three things: the smartphone's inbuilt passcode/touch-id, an additional second passcode required when entering into the app, and the physical security through your possession of the phone. This protection through Ai-Fi Central is foolproof for all intents and purposes as long as you are in possession of your smartphone. In the unfortunate event of losing your phone, your Ai-Fi data may be "wiped" along with all other mobile data on your phone. Your data won't end up in the wrong hands as long as the "wipe" is triggered in time. After the wipe, all your Ai-Fi assets are still recoverable by fetching and applying your Ai-Fi recovery passphrase for your Ai-Fi Wallet saved at the initial installation of Ai-Fi Central. (Apple iCloud would take care of the rest if you are on an iPhone, in which case you need to submit your iCloud password to enter.)
There obviously exists a window of vulnerability between the time of losing your phone and the time it is wiped and later on its content recovered, depending heavily on the strength of your Touch ID, Face ID, passcodes, or passwords. This window may be unacceptably long, especially when the loss event is the consequence of a "targeted" attack that swiftly turns off the power before taking the phone to an attack lab for offline analysis. Your Ai-Fi Central app remains vulnerable until the app is "recovered" by the original recovery passphrase and then "rekeyed" to disable or invalidate previous DigiVault and key stores.
For the rich and paranoid who are not comfortable with putting all eggs in one device, Ai-Fi offers another protection mechanism based on the latest Threshold Signature technology that fights off this "Single Basket Attack" by making use of redundant components, which involves two independent crypto transaction signers.
Passcodes and Private Keys
Not many of us are fans of the classic login/password scheme. Fortunately, underlying all the Ai-Fi protection mechanisms is the application of PKI (Public Key Infrastructure) at a strength level comparable or stronger than that protecting all the cryptocurrencies and Bitcoins in particular, achieving the pseudonymity at the same time. This lifts us out of the stone age of passwords. It also works smoothly with and in complement to any multi-factor authentication schemes.
Modern protection scheme of one's digital assets based on Public Key Cryptography is considered foolproof. The success of Bitcoin and other cryptocurrencies are directly accredited to this technology. Clearly, its effectiveness hinges on the practice of safeguard our private keys. Even though considered stronger than passwords, private keys must be physically recorded since they are too long to memorize.
In the case of cryptocurrency wallet, the ingenious scheme of condensing all the keys under a deterministic hierarchy (BIP-0032) compresses all the private keys to a single "mnemonic seed", with or without additional passphrase, for recovery, which is usually in 12 or 24 words and is still beyond the grasp of our memory. This mnemonic seed, therefore, also creates a "hot potato" issue, outside the wallet protection schemes. Most of the apparatus on the market for "saving" them are not much more than a "paper vault". (Shamir's Secret Sharing is adopted sometimes if its complexity is considered tolerable relative to the asset values to be protected.)
For those critical "hot potato" long private keys or seed phrases, Ai-Fi.net offers a user-friendly secret locking scheme of comparable (or stronger) cryptographic strength as those private keys. This secret locking "Crypton" scheme is based on the combination of strong "passphrases" of sufficient entropy and client-side "Entropy Extender", mechanically similar to the traditional "salt". You may want to learn more about this in the rather lengthy document here, including a Bug Bounty program to attest its validity and robustness. It is also documented in some depth in the context of our Ai-Fi Counterseal Wallet framework. We also offer a tool set to help you recall your passphrases, within reason, in case of minor memory lapses or mishaps due to imprecise spellings.
Password Management
Self-reliance
As practitioners of various Ai-Fi Security tools, some of us at Ai-Fi.net have gradually developed a personal approach towards the protection of a large number of passwords collected during the long stretch of time as we surf the web, connect to various Internet services and deal in various crypto currencies. Instead of relying on some third-party password management services, we are of the opinion that for privacy protection and warrant-proof guarantees self-reliance is the best policy by taking advantage of the Ai-Fi protection without involving account-based third-party service providers. We believe that Ai-Fi has developed a solid foundation for achieving the goal of self-sufficiency. However, this is not to preclude the adoption of those password management cloud services if we are clear on what we are getting into. The application of Ai-Fi password protection requires slightly more care, as privacy and security often do and demand more on our part.
Passwords as Digital Assets
The objective is to protect the following common categories of digital assets:
- All the websites we've visited and signed up for an account.
- Other non-browsing sites or software packages requiring log-in, such as ssh, skype, IM, various mobile apps, etc.
- The recovery seeds of various crypto wallets we own, including the Ai-Fi Wallet in which we store our DiD (Decentralized Identifiers). We could always write them down and figure out a place to safekeep them. Alternatively, we recommend storing them as the Cryptons.
- The PIN codes of our smartphones or hardware wallets.
The first category is where most of the password managers focus on with the Autofill option. Since one's passwords are stored and automatically filled when needed, it is a good idea to also delegate to those password managers to suggest strong passwords to avoid trivial weaknesses.
For applications in category 2, most password managers don't offer much since there is no standard to go by in identifying the password data entry in order to automatically enter the appropriate passwords. The best those utilities can offer is just a repository for password record keeping. Our Ai-Fi Central has the DigiVault embedded in our mobile app as a handy repository for this category.
Category 3 is important if one dabbles in cryptocurrencies. The recovery seeds described above are highly critical to our financial security, especially those of us who don't want to outsource the care of our cryptocurrencies to third-party escrow services. This is one of those "hot potato" issues when "paper vault" is simply too risky and outsourcing them to some third-party password manager services is unacceptable. Otherwise put, this category helps protect all those items in the "paper vault", such as the master password for your password managers.
This write-up is to document our strategy in safekeeping all these four categories of digital assets by applying those foundational services we have built into Ai-Fi Central and leveraging a few public and free password managers:
- Cryptons offered by the Ai-Fi Incognito Cloud. This safekeeping tool has the comparable strength as the private keys of your Bitcoin account.
- SuperLock, especially the multi-share secret distribution based on the classical Shamir's Secret Sharing.
- "Autofill" utilities such as those built into Google Chrome or iOS, with comparable and competitive features with most of the password managers.
- Non-web account passwords.
1 and 2 above are supported primarily through the Ai-Fi Central mobile app.
Please follow their respective documentation for details on Ai-Fi Cryptons and SuperLock.
Hierarchy of Passwords
Organizing Passwords

Lacking a methodology and giving enough rope, we inevitably hang ourselves with the self-inflicted chaos owing to the undisciplined hoarding of large amounts of passwords.
To get out of this mess, we'd recommend keeping around only a couple of strong "master" passwords and derive the rest by combining them or leveraging other utilities such as Ai-Fi DigiVault. We'd suggest the use of those "master" passwords to unlock the recovery seed for your Ai-Fi Wallet in your Ai-Fi Central app or your Cryptons in the Incognito Cloud managed independently from your Ai-Fi Central app, and derive other secondary passwords from those primary repositories.
This is an effective scheme to organize our passwords and made popular by many password managers on the market. We simply push this method one step further so our users don't need to rely on any third-party service providers (and the hazards entailed) with all the conveniences to boot. The Ai-Fi framework is itself a self-managed password manager.
Most of us are comfortable in outsourcing those secondary ones to some "Autofill" utilities offered by Google or Apple and just make sure we maintain safely the password for logging into those services. They are effective password managers if the risk of exposing your passwords to the providers is manageable. Keep in mind that it is probably unlikely for Google or Apple to engage in any active attacks on individual accounts unless they are compelled to do so by state actors. This is especially true for Google after its embarrassing account breach in 2018. For banking or financial websites, this leverage of the "Autofill" tool is recommended only if those banks and financial institutions offer 2-factor authentication so your accounts may be tied to your other email accounts or mobile phones, in addition to the auto-filled password protection. Obviously this second factor must not be part of the same "Autofill provider" in order to rule out the providers as a potential threat/vulnerability. This applies to all other non-financial sites deemed critical enough to warrant multi-factor protection.
For those adopting Google Chrome browser as the "password manager", make sure your Google account password is changed to a new password of proven strength and embrace all the security mechanisms offered by Google, including all their security schemes involving your cell, additional email address, Google Authenticator, etc. for multi-factor protection, regardless if your email address showing up in the famous ";--have i been pwned?" site or not. In the case of your email previously "pwned", you may want to sign up for a new email account in order to be severed from all the possible PII and metadata exposures due to previous breaches. With the Autofill feature, there is no reason not to adopt a very strong password.
If one takes advantage of those "Autofill" utilities or password managers built into a computing platform (e.g. Apple iOS) or embedded within the browser, there is little need to sign up for any cloud services to manage your passwords.
Composition of Passwords
One common issue of utilizing passwords is the memory lapse frequently inflicted upon us in the effort of memorizing our passwords. There should only be a small number of passwords to commit to memory. Keeping those passwords organized could go a long way. Our suggestion is to organize them hierarchically.
Sometimes we forget some passwords due to their infrequent use. This issue may be alleviated by taking advantage of the fact that the longer the password, if created intelligently, the stronger the protection. There is no reason to create all kinds of long ones just to make them stronger, at the risk of memory lapse. We could create password subcomponents of sufficient strength for their use cases, and create a long one for more crucial applications by piecing several together.
For ease of recall, structure our passwords as phrases of multiple words that are easy to remember. Most decent websites now allow the entering of blanks for structuring your password as phrases.
This will become clear in the examples below.
Example
- The most frequently used password (P1): For most of us IT guys, we enter passwords into our PC platforms or handheld devices numerous times a day. Make sure you use a strong but short and sweet one for this purpose. Instead of adopting characters of uniform cases, try something like "Wi-Fi.net" with upper/lower cases, "-" and ".", which beef up the strength significantly. Use a password strength meter. Make sure you take advantage of phrases or sentences, not just character sequences. When the password field doesn't accept blanks, relegate it to lower tiers. A service site doesn't accept blanks in its password entry field, it's not a security-conscious site. If you are the mobile phone types, make sure to strengthen your passcode to more than 4 to 6 numbers. Search this "Passcode Option" under iOS for instance.
- A good percentage of us rely on their smartphones almost exclusively without signing into a desktop or notebook anymore. In this case, there aren't many opportunities for us to practice the memorization of our passphrase. One suggestion is to make sure we turn on a longer password (Custom Alphanumeric Code in iPhone). Instead of just using 4-digit or 6-digit code, adopt the "Custom Alphanumeric Code" and make it stronger enough to implement what has been suggested in 1 above. Make sure you fully understand the risk entailed if this practice is not followed.
- The second most frequently used password (P2): This is required for those "Autofill" utilities such as Google Chrome or iOS as part of the account set up. Unfortunately, Google for one frequently offers the "Auto Sign-in" convenience allowing automatic log-in on the same platform and application without forcing the password entry every time. This is OK for Google apps, as those passwords are usually resettable to a new password when lost (but the original password is not recoverable). This is something we don't usually need to memorize as long as there is a remedy as part of the 2-factor (and other security questionnaires). The consequence is that we don't get to practice our password memorization. However, at least in the case of Gmail, even when one is unable to recall their Sign-in password, one can log out of the gmail, get back in again by selecting the Google account email (the one for the "website" myaccount.google.com) and allow the gmail Autofill the password so we can get back our original password.
- Use the concatenation of P1 and P2, optionally adding a salt as passphrases, for your most crucial password application. The salt can be written down, as long as P1 and P2 combined are sufficiently strong and not easily forgotten.
P1 is something we are all very familiar with and entered into our desktop or laptop multiple times a day if the screen timeout is configured for power and security.
P2 is easily retrieved, especially when the "Autofill" and the "Auto Sign-in" utilities offer a sync option over multiple devices through the network. Many of us take advantage of what Google offers through Chrome browser.
The "salt" adds additional entropy against online hacking if not exposed. It may also be comfortably written down and kept in a drawer. For this reason we call it "Entropy Extender".
A Password Strategy for Practitioners
The following is an example strategy for safekeeping your passwords:
- Create the password P1 of sufficient strength based on the password evaluator. Preferably see all "guess times" as "centuries". Your daily work hours offer ample opportunities for you to exercise this important P1.
- Browse with Chrome. Use it as a password manager for website visits that require sign-in. Create a strong password as P2 and make sure it is being exercised at least once daily (by turning off "Auto Sign-in") or by taking advantage of the "Autofill" function during re-sign-in after signing out.
- For your cryptocurrencies, if not outsourced to an escrow service, concatenate P1, P2, and the "Entropy Extender" into a new password phrase. In the context of Ai-Fi.net, apply this as the Crypton key for recovering the wallet "recovery/seed passphrase". In the event of wallet loss, all the database content, including the DigiVault, email encryption keys, SuperLocks, and other data, can be recovered.
- For other non-web applications or standalone apps, use the DigiVault offered by Ai-Fi Central. The wallet and other digital assets in the Ai-Fi Central app are recoverable as described above.
The P1 above takes centuries to crack if attacked offline without throttling. P2 is entered and protected by Google cloud. Although both are used daily on Windows 10 platform in our example, their compromise is still a possibility. However, the combination of P1, P2 and extra Entropy Extender thrown into the mix at the creation of the Ai-Fi Crypton appears indestructible.
In summary, to ward off identity theft, design an indestructible seed/recovery passphrase, memorize it, supplement it with an Autofill tools like iPhone or Google Chrome for web accounts, use 2-factor for critical (bank or any sites involving money) accounts, and diligently record all your non-web passwords in the Ai-Fi DigiVault.
Password Strength Meter
Principle of Password Cracking
The principle behind all password or passphrase cracking is quite straightforward. The first step is to collect all the raw or base materials, namely those which have been cracked in the past. Before we start to be a bit more defensive about the attacks on our passwords, we tend to use a few that we feel comfortable with without giving much thought to them. They tend to be short and easy to memorize, created based on some naive notion of their "strength", most of which are wrong and misleading, including those originally suggested by NIST. At the same time a large number of web services are quite negligent in handling our passwords we've trusted to their care. We rarely get any compensation other than some "apologies" from those service providers after password breaches. This casual attitude on both sides has led to an ungodly amount of our passwords cracked or stolen by hackers and available openly for anyone to collect for a nominal fee. You will not be surprised to find your precious few passwords recorded as "pwned" by visiting the "Have I been Pwned" site. Those pwned passwords are numbered in the tens of billions.
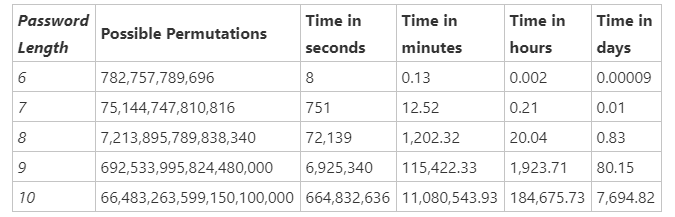
After getting their hands on those pwned passwords, the hacking steps are simply to try the collection one by one, applying some known "rulesets" with each entry (e.g. capitalizing the first letter, replacing "o" with "0", suffixing some number of digits, etc.). If Amazon AWS is hired for this cracking effort, the number of stolen passwords to try per second can be roughly calculated as 1-billion entries at the cost of $1.
Other than those pwned base words, all known publications including dictionaries, bibles, journals, newspapers, Kindle books, and famous quotes have all been collected to form part of the base words arranged in projected frequency of use.
The password cracking is basically a shortcut to explore the immense (search) space of possible passwords. The approach above is for untargeted attacks, where there is no known person or target to aim at. However, if we have a specific target in mind, some simple but efficient approach can be designed by collecting the target's name, nickname, phone#, DOB, name of family members, their employer's web site, whitepapers, manuals, vocation specific technical vocabulary, neighborhood specific maps, etc. For us network security practitioners, we have difficulty getting away from words like protocol, protects, privacy, ai-fi, etc. As a consequence, the following guideline is quite difficult to follow:
- Known only to you
- Long enough to be secure
- Hard to guess – even by someone who knows you well
- Easy for you to remember
- Easy for you to type accurately
An obvious alternative is to adopt Diceware at the expense of ease of memorization. It uses ordinary dice to select words at random from a special list called the Diceware Word List. The random selection of words breaks free from the classical cracking schemes described previously which relies on customary and predictable patterns of password selections to pare down the search space. Note that our Entropy Extender provides one such random string allowing arbitrary length, which may be written down in a notebook, safely protected by our password.
zxcvbn and Password Meters
There are numerous password strength testers on the web. Some of those are suspected to be rogue password collectors, so take precaution when testing out there. Our recommendation is the well known password evaluator zxcvbn site, backed by a technical paper and YouTube presentation with Dropbox behind them. The nice thing about this tester is that it gives critique after the test pointing out the weakness of your passwords.
zxcvbn gives test results based on different attack scenarios. The online attacks apply to our typical sign-in with passwords, which is mostly "throttled" to limit your number of tries per unit time. The offline attacks apply to scenarios when your computing devices were stolen or fell in the hands of attackers, including the many situations when the service providers are compromised that renders the throttling useless.
After playing around with this tester for a while, a few rules seem to emerge. Length is all critical with a minimum of 12 characters, all else doesn't have a prayer, as echoed in this Microsoft report.
There are a few pointers we have collected from playing around this utility. Sprinkle funny characters and vary letter cases liberally. Repeating or predictable patterns are not effective means of lengthening. A phrase with multiple words separated by blanks works well to achieve long password by utilizing a narrative or story telling. For example, "This is my master password part 1" (literally) gets "centuries" in all four categories in the zxcvbn tester. Obviously, the suggested practice of "This is my master password part 1" + "This is my master password part 2" will take at least "centuries x centuries" to crack.
You will find it rewarding to play around with the passphrases/passwords easy for you to memorize and then try to simplify it but maintain the same strength. For instance,
- "Ai-Fi.net protects my privacy" may be simplified to "aifinet protects my privacy" but much easier to type in. In anticipation of "Ai-Fi" becoming a household name and targeted attacks, we adopt zifinet instead.
- "google protects my privacy": This oxymoron has the same strength as the one above. The length of the phrase is all critical. There is no funny letters or anything requiring the "shift" key appearing in it, easy on the fingers. "zifinet protects my privacy google protects my privacy" is long winded and with repeating words, however, it is easy to memorize and gets "Centuries" score on all four categories by the zxcvbn evaluator.
- "?Out//look\\" is much weaker than "Facebook sucks?". The first contorted password pattern is hard on us humans, but fails to impress the password cracker. The diplomatic "?" in the second pattern has gotten us quite a bit extended mileage.
- zxcvbn assigns low scores to words of high usage frequency. This is consistent with the classical attack scenarios where high frequency words are more likely to recur in those pwned collections. However, as all other password strength meters, it relies on various heuristics in making educated guesses on how the candidate passwords are formulated in users' brains. Those heuristics are as varied as the models they are based on and their dictionary sizes. For instance, both the "one two three four five six" and "how much wood could a woodchuck chuck if a woodchuck could chuck wood" both obtain "centuries" on zxcvbn's scoreboard, which are quite ludicrous with serious consequences if taken on as seed passphrase for Bitcoin wallets.
The Revised Strategy
The efficacy of the memorization strategy laid out here has been proven highly helpful, except those passphrases being used daily. They have been replaced by some different set of passphrases which seem to survive better the test of time based on an alternative tried and true memorization technique.
MiniLock Key Stretching
The passwords collected at the service providers' typically trigger a run of some hashing logic, which can be further extended as a "key derivation" function. The key derivation hash function achieves the biggest gain, maximizing the ratio of crack time from 1 to 100,000 with Argon2 as the preferred algorithm. The client-side salt is also a big winner in thwarting the dictionary attack and injecting entropy into the fray without taxing our rain too much. Ai-Fi.net offers all options in terms of key stretching and salt for our users to adjust their creation of master passphrases. Make sure you understand why we throw in many options and adopt the appropriate level of security per intended application.
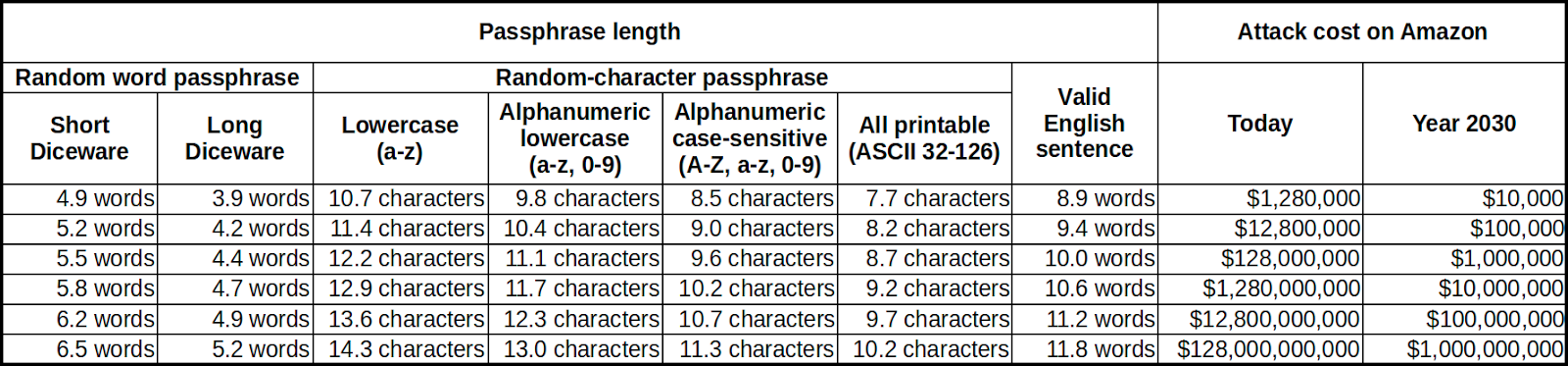
Securing the Passphrases
Our Raw Memory Capacity
As has been suggested, the best approach to secure our secret is to tie them to a mental mechanism requiring our entering of a high-entropy passphrase to open it.
The concern for self-maintained passphrases is their cryptographic strength and our ability in reliably memorizing them. Even for conscientious users who want to maximize the protection of passphrases, its strength tops out at around 100 bits of entropy if requiring memorization. Deciding on a secure passphrase for secret preservation is a tug of war between the ease of memorization and their built-in entropy. Some additional facilities are needed to boost their strength when deemed necessary.
We will be offering some suggestions about how we can improve our ability in memorizing our passphrases that we find useful.
The Memory Code of Imagery
Modern humans suffer a severe case of memory atrophy. We compensate for this particular atrophied brain function by many memory aids, such as pen and pencil, maps, computer storage, notebooks, password manager, etc. The smartphones have undoubtedly accelerated its pace of deterioration. Those memory aids work adequately in most cases except when we need to keep some information to ourselves as secrets. Passwords are the obvious examples, any tangible records of which may jeopardize their purpose of existence. Secrets, by definition, are not supposed to be outsourced. The promise of decentralization and our independence from surveillance capitalism require some minimal efforts on our part. A tiny amount of memorization appears to be inevitable.
Our memory capacity has not been this weak in the past. As a matter of evolution, we have all been champions of memorization until recently. The North American Navajo, for example, named and classified over 700 species of insect by memory. The African Dogon systematically classified about 300 vegetables. The Hanunóo in the Philippines named many more plants for the region than did Western science when botanists worked with them in the middle of the twentieth century. The Matsés peoples of Brazil and Peru have recently documented their traditional medicine in a 500-page encyclopedia to ensure the information is not lost. Before it was written down, their entire corpus of Amazonian plant knowledge was stored primarily in memory. In contrast, our modern day white-collar workers need to write down their password on a post-it and stick it to the back of their computer before losing it.
Many linguists believe all human languages derived from a single tongue spoken in East Africa around 50,000 years ago. Between the birth of this "proto-human language" and the invention of papyrus for recording words around 5000 BCE, we humans had managed to create, maintain and communicate a vast amount of knowledges shared among ourselves, and our communities had evolved from hunter-gatherers to an agricultural society with extensive human interaction for passing down vital information including seasonal changes; astronomical events; patterns among the stars; land management and irrigation plans; shaman practices; medicinal plants; animal identification and behavior; law and ethics; genealogies; and countless other uniquely human experience that made us the dominating species on the planet. We had accomplished these amazing feats all without relying on any literate implements or writing materials, We Homo sapiens took full advantage of our memory faculty in that long period of time without written words and still managed to flourish.
Our memory does not work like a video camera, but an associative machine that distributes (encodes) different aspects of our experience and ideas, real or imaginary, to various functional parts of the brain for easy retrieval when needed. The key to memorization is not rote repetition but breaking apart the subject matter methodically and archiving subparts into our brain organically. It is believed that our ancestors in those earlier non-literate vocal cultures had developed an extraordinary ability to encode vast amounts of information using a wide range of memory aids through the ancient mnemonic technologies of "memory spaces".
Applying the same methodologies, modern day memory competition champions can memorize 616 random numbers in 5 minutes, a deck of cards in 12.74 seconds, and 335 words in 15 minutes. For protecting our Cryptons, we only need to memorize a measly 4 to 6 "random" words. That ought to be a cinch even under the severe threat of atrophy of our memorization faculty. We just need to recover the lost art of ancient memorization technologies. After viewing a highly instructive video: https://www.youtube.com/watch?v=JbLAGpQ9RXg, most of us manage to memorize the passphrase "mother butter apple coffee blossom", apparently totally random, in 1 minute. The following picture has been easily and firmly imprinted in most viewers' memory:

Interesting enough, the opposite is often true. It can become a challenge trying to erase this very picture from your memory. Once it is seen, it can't be easily unseen.
Better yet, the phrase can be extended longer still without much additional effort (e.g. placing more things on the folding table or releasing some animals on the lawn). Imagery is so much easier to retain in memory and perfectly in tune with how our brain works.
The Memory Code of Context
Our ability of conceiving an ad hoc imagery for the placement of objects to be memorized may not be as sharp as we want. A different mental apparatus based on familiar spatial environments is known as memory palace, memory journey, or method of loci. It relies less on imagery, but more on depositing items to objects in a familiar landscape or route. When desiring to remember a set of items the subject 'walks' through these loci in their imagination and commits an item to each one by forming an image between the item and any feature of that locus. The method relies on memorized spatial relationships to establish order and recollect memorial content. The "palace", loci, journey, landscape or route in this approach is as fixed and permanent as possible in order for our imaginations to anchor on. Some scholars suggest Stonehenge is actually one such "palace". It can even be built upon something portable as the "lukasa" pictured on the below right.

We found this short training video helpful: https://www.youtube.com/watch?v=PIbz_gKw0XY. The science behind it can be found here. After months of using our previous set of passwords "aifinet protects my privacy" and "google protects my privacy", we found them to fade rather quickly, as both are based on rather abstract concept without concrete contexts to hang (literally) those concepts on. They seem to escape from our brains easily. On the other hand, the phrase "disney BLM Main deck" has passed the test of time since they are first created and tightly attached to an area in Los Angeles we frequently hang out. There is no substitute for real-life experience attached to signaficant and tangible context (pictures) as far as memory goes. A picture is worth a thousand words, literally.
As a side note, those palaces and lukasa are memory aids and persistent fixtures by design. They become useful and intelligible only after we instill live content into them. This may be the reason why the Stonehenge and many sites like it had become archeological mysteries after we collectively lost their original contents.
The Real Strength Test
The effort required to memorize passwords is much lighter than those traditional memorization tasks of recording real objects and factual events. All we need to do is to fabricate an imaginary context to aid our memorization of passwords.
Unlike those ancient memory techniques aimed mainly for recording knowledge and history, we have considerable latitude in creating and memorizing our secret passphrases. We don't need them to match rigorously with any real objects or events as long as they exhibit a high degree of randomness to people not in the know and easy retrievability when needed. If the "palace" itself grows out of our own personal environment, like the layout of our homestead or the walk in our neighborhood, and some of the objects or concept we commit to individual feature of the loci emerge by happenstance (but "memorable"), the randomness aspect of the requirement is easily satisfied. Let's look at an example: "disney BLM Main deck" based on a walk route in downtown Los Angeles, where "disney" sources from Walt Disney Concert Hall on 1st and Grant, "BLM" a protest rally taking place in front of the LAPD Headquarters a while ago, "main" is the street where the City Hall is on, which offers a landmark of high and beautiful observation "deck" for the best view of Los Angeles cityscape (free of admission charge to boot). This 4-word passphrase is reasonably strong for our purpose and not too shabby compared to Diceware. It is indestructible if further augmented with our "Entropy Extender".
For any "random" collection of words, there are a few excellent sites that will verify its strength. For example, we've found the following site quite professional and capable:
- https://www.onlinehashcrack.com
- https://emn178.github.io/online-tools/sha256.html: This is to enter your passphrase to get the output hash in desired format, which you enter into the previous onlinehashcrack.com for password cracking.
We have submitted 2 passphrases, each consisting of 4 "words" created during our first few experiments with those memory crafts introduced by some YouTube videos, spending less than 30 minutes total. Both passed the onlinehashcrack.com test after rigorous crack efforts in 3 days continuously.
The Fuzzy Search Utility
Sometimes we do suffer some memory lapse and only remember the gist of the context where the passphrases are first created. For instance, the picture resented previously with cherry blossoms may not trigger the exact recall of the phrase "mother butter apple coffee blossom". However, we still remember the vivid picture with all the objects in it, except we may not recall the order of words or the exact number of objects in the phrase (for example, is the butter churner, the green grass or the side table part of the phrase?). Some of the syntactic rules may also no longer be retrievable, such as the capitalization of the involved words. In those cases we tend to explore various possibilities trying to recover it, especially when a large sum of cryptocurrencies is involved. The permutations of words would grow to a large number rather quickly.
For password recovery in those cases, we have designed a utility to ease your trial and error by offering a special mode of "Fuzzy Search", under which you only need to offer a list of words and checkbox a few simple rules such that the trial and error would be automated by this utility. This Fuzzy Search still requires the memory aids you have employed at the creation of the password. The utility presumes that the pictures or the memory palace is still uniquely yours and we only permute through the possibilities to compensate for the fuzziness.
This is obviously assuming that the passphrase and its original context remain secure without leakage. The only help one needs is to recover the exact number of words in the password and their order.